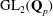 ${\rm GL}_2(\mathbf{Q}_p)$,
${\rm GL}_2(\mathbf{Q}_p)$, 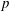 $p$-adic automorphic forms, and the canonical embedding of Shimura curves
$p$-adic automorphic forms, and the canonical embedding of Shimura curves
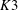 $\def \xmlpi #1{}\def \mathsfbi #1{\boldsymbol {\mathsf {#1}}}\let \le =\leqslant \let \leq =\leqslant \let \ge =\geqslant \let \geq =\geqslant \def \Pr {\mathit {Pr}}\def \Fr {\mathit {Fr}}\def \Rey {\mathit {Re}}K3$ surfaces with real multiplication
$\def \xmlpi #1{}\def \mathsfbi #1{\boldsymbol {\mathsf {#1}}}\let \le =\leqslant \let \leq =\leqslant \let \ge =\geqslant \let \geq =\geqslant \def \Pr {\mathit {Pr}}\def \Fr {\mathit {Fr}}\def \Rey {\mathit {Re}}K3$ surfaces with real multiplication
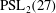 $\mathrm{PSL}_2(27)$ in the Monster
$\mathrm{PSL}_2(27)$ in the Monster
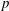 $p$-subgroups of finite Chevalley groups of rank six and seven
$p$-subgroups of finite Chevalley groups of rank six and seven
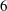 $\def \xmlpi #1{}\def \mathsfbi #1{\boldsymbol {\mathsf {#1}}}\let \le =\leqslant \let \leq =\leqslant \let \ge =\geqslant \let \geq =\geqslant \def \Pr {\mathit {Pr}}\def \Fr {\mathit {Fr}}\def \Rey {\mathit {Re}}6$-coverings of elliptic curves
$\def \xmlpi #1{}\def \mathsfbi #1{\boldsymbol {\mathsf {#1}}}\let \le =\leqslant \let \leq =\leqslant \let \ge =\geqslant \let \geq =\geqslant \def \Pr {\mathit {Pr}}\def \Fr {\mathit {Fr}}\def \Rey {\mathit {Re}}6$-coverings of elliptic curves