114 results in 68Qxx
On ε-Optimality of the Pursuit Learning Algorithm
- Part of
-
- Journal:
- Journal of Applied Probability / Volume 49 / Issue 3 / September 2012
- Published online by Cambridge University Press:
- 04 February 2016, pp. 795-805
- Print publication:
- September 2012
-
- Article
-
- You have access
- Export citation
Testing commutativity of a group and the power of randomization
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 15 / May 2012
- Published online by Cambridge University Press:
- 01 April 2012, pp. 38-43
-
- Article
-
- You have access
- Export citation
Gröbner bases for quadratic algebras of skew type
- Part of
-
- Journal:
- Proceedings of the Edinburgh Mathematical Society / Volume 55 / Issue 2 / June 2012
- Published online by Cambridge University Press:
- 16 March 2012, pp. 387-401
-
- Article
-
- You have access
- Export citation
Muller condition and fairness on multitransition systems
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 14 / 2011
- Published online by Cambridge University Press:
- 01 April 2011, pp. 99-107
-
- Article
-
- You have access
- Export citation
Growth in Baumslag–Solitar groups I: subgroups and rationality
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 14 / 2011
- Published online by Cambridge University Press:
- 01 February 2011, pp. 34-71
-
- Article
-
- You have access
- Export citation
Constructing maximal subgroups of orthogonal groups
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 13 / January 2010
- Published online by Cambridge University Press:
- 01 May 2010, pp. 164-191
-
- Article
-
- You have access
- Export citation
Une dualité entre fonctions booléennes
- Part of
-
- Journal:
- Journal of the Institute of Mathematics of Jussieu / Volume 9 / Issue 3 / July 2010
- Published online by Cambridge University Press:
- 26 April 2010, pp. 633-652
- Print publication:
- July 2010
-
- Article
- Export citation
A Stochastic Maximin Fixed-Point Equation Related to Game Tree Evaluation
- Part of
-
- Journal:
- Journal of Applied Probability / Volume 44 / Issue 3 / September 2007
- Published online by Cambridge University Press:
- 14 July 2016, pp. 586-606
- Print publication:
- September 2007
-
- Article
-
- You have access
- Export citation
Monte Carlo Algorithms for Finding the Maximum of a Random Walk with Negative Drift
- Part of
-
- Journal:
- Journal of Applied Probability / Volume 43 / Issue 1 / March 2006
- Published online by Cambridge University Press:
- 14 July 2016, pp. 74-86
- Print publication:
- March 2006
-
- Article
-
- You have access
- Export citation
A mosaic of triangular cells formed with sequential splitting rules
- Part of
-
- Journal:
- Journal of Applied Probability / Volume 41 / Issue A / 2004
- Published online by Cambridge University Press:
- 14 July 2016, pp. 3-15
- Print publication:
- 2004
-
- Article
- Export citation
An almost sure result for path lengths in binary search trees
- Part of
-
- Journal:
- Advances in Applied Probability / Volume 35 / Issue 2 / June 2003
- Published online by Cambridge University Press:
- 22 February 2016, pp. 363-376
- Print publication:
- June 2003
-
- Article
- Export citation
Average case behavior of random search for the maximum
- Part of
-
- Journal:
- Journal of Applied Probability / Volume 34 / Issue 3 / September 1997
- Published online by Cambridge University Press:
- 14 July 2016, pp. 632-642
- Print publication:
- September 1997
-
- Article
- Export citation
On the transition probabilities of the move-to-front scheme
- Part of
-
- Journal:
- Journal of Applied Probability / Volume 31 / Issue 2 / June 1994
- Published online by Cambridge University Press:
- 14 July 2016, pp. 570-574
- Print publication:
- June 1994
-
- Article
- Export citation
Scheduling and stability aspects of a general class of parallel processing systems
- Part of
-
- Journal:
- Advances in Applied Probability / Volume 25 / Issue 1 / March 1993
- Published online by Cambridge University Press:
- 01 July 2016, pp. 176-202
- Print publication:
- March 1993
-
- Article
- Export citation

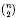 quadratic relations of certain type, which includes the class of monoids yielding set-theoretic solutions of the quantum Yang–Baxter equation, also called binomial monoids (or monoids of I-type with square-free defining relations). It is shown that under any degree-lexicographic order on the associated free monoid FM
quadratic relations of certain type, which includes the class of monoids yielding set-theoretic solutions of the quantum Yang–Baxter equation, also called binomial monoids (or monoids of I-type with square-free defining relations). It is shown that under any degree-lexicographic order on the associated free monoid FM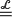 ξ max
ξ max