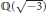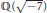16 results
4 - On Encryption Technologies and Potential Solutions for Lawful Access
- from Part I - Collecting Digital Evidence
-
-
- Book:
- The Cambridge Handbook of Digital Evidence in Criminal Investigations
- Published online:
- 02 January 2025
- Print publication:
- 09 January 2025, pp 104-125
-
- Chapter
- Export citation
9 - Cryptographic Theory and Decentralized Finance
- from The Third Era
-
- Book:
- A History of Financial Technology and Regulation
- Published online:
- 24 March 2022
- Print publication:
- 31 March 2022, pp 112-128
-
- Chapter
- Export citation
1 - Introduction
-
- Book:
- Computational Cryptography
- Published online:
- 11 November 2021
- Print publication:
- 02 December 2021, pp 1-12
-
- Chapter
- Export citation
11 - History of Cryptographic Key Sizes
- from Part II - Implementations
-
- Book:
- Computational Cryptography
- Published online:
- 11 November 2021
- Print publication:
- 02 December 2021, pp 314-334
-
- Chapter
- Export citation

The Hidden Language of Graphic Signs
- Cryptic Writing and Meaningful Marks
-
- Published online:
- 23 August 2021
- Print publication:
- 19 August 2021
Three - Impossible Unities
- from Part I - Hidden Writing
-
-
- Book:
- The Hidden Language of Graphic Signs
- Published online:
- 23 August 2021
- Print publication:
- 19 August 2021, pp 54-79
-
- Chapter
- Export citation
Seven - Marking and Writing in an Egyptian Workmen’s Community
- from Part II - Legible Signs
-
-
- Book:
- The Hidden Language of Graphic Signs
- Published online:
- 23 August 2021
- Print publication:
- 19 August 2021, pp 159-172
-
- Chapter
- Export citation
2 - The Technology of the Blockchain
- from Part I - The Blockchain
-
- Book:
- Blockchain Democracy
- Published online:
- 16 January 2020
- Print publication:
- 02 January 2020, pp 41-60
-
- Chapter
- Export citation
5 - Supersingular isogeny graphs in cryptography
-
-
- Book:
- Surveys in Combinatorics 2019
- Published online:
- 17 June 2019
- Print publication:
- 27 June 2019, pp 143-166
-
- Chapter
- Export citation

Surveys in Combinatorics 2019
-
- Published online:
- 17 June 2019
- Print publication:
- 27 June 2019
AN EFFICIENT METHOD FOR IMPROVING THE COMPUTATIONAL PERFORMANCE OF THE CUBIC LUCAS CRYPTOSYSTEM
- Part of
-
- Journal:
- Bulletin of the Australian Mathematical Society / Volume 90 / Issue 1 / August 2014
- Published online by Cambridge University Press:
- 10 April 2014, pp. 160-171
- Print publication:
- August 2014
-
- Article
-
- You have access
- Export citation
A tight bound for exhaustive key search attacks against MessageAuthentication Codes
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 47 / Issue 2 / April 2013
- Published online by Cambridge University Press:
- 06 November 2012, pp. 171-180
- Print publication:
- April 2013
-
- Article
- Export citation
On the joint 2-adic complexity of binary multisequences∗
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 46 / Issue 3 / July 2012
- Published online by Cambridge University Press:
- 06 April 2012, pp. 401-412
- Print publication:
- July 2012
-
- Article
- Export citation
Nonadjacent Radix-τ Expansions of Integers in Euclidean Imaginary Quadratic Number Fields
-
- Journal:
- Canadian Journal of Mathematics / Volume 60 / Issue 6 / 01 December 2008
- Published online by Cambridge University Press:
- 20 November 2018, pp. 1267-1282
- Print publication:
- 01 December 2008
-
- Article
-
- You have access
- Export citation
The accessibility of an access structure
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 40 / Issue 4 / October 2006
- Published online by Cambridge University Press:
- 08 November 2006, pp. 559-567
- Print publication:
- October 2006
-
- Article
- Export citation
Quantum Information
-
- Journal:
- MRS Bulletin / Volume 30 / Issue 2 / February 2005
- Published online by Cambridge University Press:
- 31 January 2011, pp. 99-104
- Print publication:
- February 2005
-
- Article
- Export citation