Article contents
Nonadjacent Radix-τ Expansions of Integers in Euclidean Imaginary Quadratic Number Fields
Published online by Cambridge University Press: 20 November 2018
Abstract
In his seminal papers, Koblitz proposed curves for cryptographic use. For fast operations on these curves, these papers also initiated a study of the radix- $\tau $ expansion of integers in the number fields
$\tau $ expansion of integers in the number fields 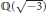 $\mathbb{Q}\left( \sqrt{-3} \right)$ and
$\mathbb{Q}\left( \sqrt{-3} \right)$ and
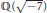 $\mathbb{Q}\left( \sqrt{-7} \right)$. The (window) nonadjacent form of
$\mathbb{Q}\left( \sqrt{-7} \right)$. The (window) nonadjacent form of  $\tau $ -expansion of integers in
$\tau $ -expansion of integers in 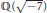 $\mathbb{Q}\left( \sqrt{-7} \right)$ was first investigated by Solinas. For integers in
$\mathbb{Q}\left( \sqrt{-7} \right)$ was first investigated by Solinas. For integers in 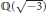 $\mathbb{Q}\left( \sqrt{-3} \right)$, the nonadjacent form and the window nonadjacent form of the
$\mathbb{Q}\left( \sqrt{-3} \right)$, the nonadjacent form and the window nonadjacent form of the  $\tau $ -expansion were studied. These are used for efficient point multiplications on Koblitz curves. In this paper, we complete the picture by producing the (window) nonadjacent radix-
$\tau $ -expansion were studied. These are used for efficient point multiplications on Koblitz curves. In this paper, we complete the picture by producing the (window) nonadjacent radix- $\tau $ expansions for integers in all Euclidean imaginary quadratic number fields.
$\tau $ expansions for integers in all Euclidean imaginary quadratic number fields.
Keywords
- Type
- Research Article
- Information
- Copyright
- Copyright © Canadian Mathematical Society 2008
References
- 10
- Cited by


