Crossref Citations
This article has been cited by the following publications. This list is generated based on data provided by
Crossref.
Barbulescu, Razvan
Gaudry, Pierrick
and
Kleinjung, Thorsten
2015.
Advances in Cryptology – ASIACRYPT 2015.
Vol. 9453,
Issue. ,
p.
31.
Pierrot, Cécile
2015.
Advances in Cryptology -- EUROCRYPT 2015.
Vol. 9056,
Issue. ,
p.
156.
Sarkar, Palash
and
Singh, Shashank
2016.
Advances in Cryptology – ASIACRYPT 2016.
Vol. 10031,
Issue. ,
p.
37.
Sarkar, Palash
and
Singh, Shashank
2016.
Advances in Cryptology – EUROCRYPT 2016.
Vol. 9665,
Issue. ,
p.
429.
Kim, Taechan
and
Barbulescu, Razvan
2016.
Advances in Cryptology – CRYPTO 2016.
Vol. 9814,
Issue. ,
p.
543.
Gaudry, Pierrick
Grémy, Laurent
and
Videau, Marion
2016.
Collecting relations for the number field sieve in.
LMS Journal of Computation and Mathematics,
Vol. 19,
Issue. A,
p.
332.
Kim, Taechan
and
Jeong, Jinhyuck
2017.
Public-Key Cryptography – PKC 2017.
Vol. 10174,
Issue. ,
p.
388.
Menezes, Alfred
Sarkar, Palash
and
Singh, Shashank
2017.
Paradigms in Cryptology – Mycrypt 2016. Malicious and Exploratory Cryptology.
Vol. 10311,
Issue. ,
p.
83.
Grémy, Laurent
Guillevic, Aurore
Morain, François
and
Thomé, Emmanuel
2018.
Selected Areas in Cryptography – SAC 2017.
Vol. 10719,
Issue. ,
p.
85.
Barbulescu, Razvan
and
Duquesne, Sylvain
2019.
Updating Key Size Estimations for Pairings.
Journal of Cryptology,
Vol. 32,
Issue. 4,
p.
1298.
Zhu, Yuqing
Wen, Jiejing
Zhuang, Jincheng
Lv, Chang
and
Lin, Dongdai
2020.
Refined analysis to the extended tower number field sieve.
Theoretical Computer Science,
Vol. 814,
Issue. ,
p.
49.
De Micheli, Gabrielle
Gaudry, Pierrick
and
Pierrot, Cécile
2020.
Advances in Cryptology – CRYPTO 2020.
Vol. 12171,
Issue. ,
p.
32.
Auerbach, Benedikt
Giacon, Federico
and
Kiltz, Eike
2020.
Advances in Cryptology – EUROCRYPT 2020.
Vol. 12107,
Issue. ,
p.
475.
Al Aswad, Haetham
and
Pierrot, Cécile
2023.
Individual discrete logarithm with sublattice reduction.
Designs, Codes and Cryptography,
Vol. 91,
Issue. 12,
p.
4059.
Zhu, Yuqing
and
Liu, Jiqiang
2023.
Constructing CM Fields for NFS to Accelerate DL Computation in Non-Prime Finite Fields.
IEEE Transactions on Information Theory,
Vol. 69,
Issue. 6,
p.
4045.
Al Aswad, Haetham
Thomé, Emmanuel
and
Pierrot, Cécile
2024.
Discrete Logarithm Factory.
IACR Communications in Cryptology,
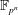 $\def \xmlpi #1{}\def \mathsfbi #1{\boldsymbol {\mathsf {#1}}}\let \le =\leqslant \let \leq =\leqslant \let \ge =\geqslant \let \geq =\geqslant \def \Pr {\mathit {Pr}}\def \Fr {\mathit {Fr}}\def \Rey {\mathit {Re}}\mathbb{F}_{p^n}$ for the whole range of applicability of the NFS and lowers the asymptotic complexity from
$\def \xmlpi #1{}\def \mathsfbi #1{\boldsymbol {\mathsf {#1}}}\let \le =\leqslant \let \leq =\leqslant \let \ge =\geqslant \let \geq =\geqslant \def \Pr {\mathit {Pr}}\def \Fr {\mathit {Fr}}\def \Rey {\mathit {Re}}\mathbb{F}_{p^n}$ for the whole range of applicability of the NFS and lowers the asymptotic complexity from 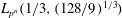 $L_{p^n}({1/3},({128/9})^{1/3})$ to
$L_{p^n}({1/3},({128/9})^{1/3})$ to 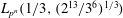 $L_{p^n}({1/3},(2^{13}/3^6)^{1/3})$ in the medium-characteristic case, and from
$L_{p^n}({1/3},(2^{13}/3^6)^{1/3})$ in the medium-characteristic case, and from 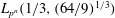 $L_{p^n}({1/3},({64/9})^{1/3})$ to
$L_{p^n}({1/3},({64/9})^{1/3})$ to 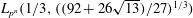 $L_{p^n}({1/3},((92 + 26 \sqrt{13})/27)^{1/3})$ in the high-characteristic case.
$L_{p^n}({1/3},((92 + 26 \sqrt{13})/27)^{1/3})$ in the high-characteristic case.