Policy Significance Statement
Digital identity policy makers are confronted with a growing set of documents, frameworks, and approaches to guide the development, implementation, and use of such systems. Each of these “digital identity principles” documents embodies the particular world views, values, and expectations of its authors and contributors. Each foregrounds some elements of the digital identity landscape while backgrounding others. However, the consequences of these different groundings are often not made explicit and can have significant policy implications, particularly in developmental contexts. This paper examines three such documents, one initiated by the World Economic Forum, another from Access Now, and a third based on contributors from the World Bank, GSMA (the mobile industry’s member organization) and the Secure Identity Alliance (an identity industry association). They represent initiatives by independent international organizations supporting public–private cooperation, industry, and civil society. The paper critically analyzes these documents in terms of their sociopolitical configurations and discusses the policy implications that arise from this analysis.
1. Introduction
There is growing recognition of the importance of identity for socioeconomic development, and this has resulted in identity becoming a key component of the United Nations Sustainable Development Goals (SDGs). Identity is seen to have a particular developmental role under Goal 16 in promoting “peaceful and inclusive societies for sustainable development,” providing “access to justice for all” as well as helping “build effective, accountable and inclusive institutions at all levels”(United Nations, 2015). Specifically, SDG 16.9 seeks to provide a legal identity for all, including the estimated 1 billion individuals who currently do not have access to a formal identity. Half of this population is found in Africa and lack of a legally recognized identity disproportionately affects vulnerable populations, such as the poor, people living in rural and remote areas, marginalized women and children, stateless persons, migrants, and persons with disabilities (Harbitz and Tamargo, Reference Harbitz and Tamargo2009; World Bank, 2021a).
The fact that there is a developmental goal is the acknowledgement of the importance of identity systems are increasingly important not only to the economic development of countries but also to individual rights and opportunities and social justice more generally (e.g., Harbitz and Tamargo, Reference Harbitz and Tamargo2009; Plan International, 2022). Not having an official identity condemns millions of people to anonymity and to being marginalized, because many activities—from opening a bank account to attending school to selling goods up the value chain, not to mention voting or moving within or between countries—often require proof of identity (Pokharel and Niroula, Reference Pokharel and Niroula2015). For individuals, digital identities can “open up (or close off) the digital world, with its jobs, political activities, education, financial services, healthcare and more” (World Economic Forum, 2018, p. 10).
The unequal access to reliable and usable forms of identity (both digital and analogue) highlights the importance of taking action to minimize the gap between service provision and development outcomes (McGrath, Reference McGrath2016; Martin and Taylor, Reference Martin and Taylor2021; Masiero and Bailur, Reference Masiero and Bailur2021). As a consequence, in recent years, there has been a range of initiatives to support the development of identity systems, with a particular focus on their implementation as digital systems.
These include initiatives led by intergovernmental organizations such as the World Bank (2021b), trade organizations such as the GSMA and Secure Identity Alliance (2014), and independent international organizations supporting public–private cooperation (World Economic Forum, 2018) as well as academic initiatives (Maple et al., Reference Maple, Epiphaniou and Gurukumar2021). Some of these initiatives, such as the World Bank’s identification for development program (World Bank, 2022), make this developmental focus explicit. In others, the developmental angle is often presented as one of the drivers for action (e.g., World Economic Forum, 2018; ID2020, 2022).
The significance of this developmental angle means that whilst it is broadly acknowledged that digital identity systems have significant technological components (Maple et al., Reference Maple, Epiphaniou and Gurukumar2021) it is important to recognize that they operate within a broader sociotechnical (Sarker et al., Reference Sarker, Chatterjee, Xiao and Elbanna2019) and political economy context (Khan and Roy, Reference Khan and Roy2019; van Dijck and Jacobs, Reference van Dijck and Jacobs2020). Additionally these are always contexts where various forms of power are at play (Medaglia et al., Reference Medaglia, Eaton, Hedman and Whitley2022) and different government policies interact to influence the implementation of digital identity initiatives (Whitley and Hosein, Reference Whitley and Hosein2008), for example, in the relationship between identity for recognition and identity as a means of surveillance (Weitzberg et al., Reference Weitzberg, Cheesman, Martin and Schoemaker2021).
This paper adopts Renieris’ (Reference Renieris2021) exhortation that “we should resist the urge to narrowly scrutinise the technical contours of a given technology or system; we should instead contest the underlying imaginations that shape it, making sure to ask whose imagination it represents.” In particular it proposes an approach to better understand the implications of the imaginations and framings of digital identity principles with an emphasis on developmental contexts.
The next section of the paper introduces academic research that has studied how imaginations and framings shape the development of digital systems. It also considers developmental literature that highlights the significance of many contemporary imaginations and framings for socioeconomic development. These elements come together as a means of understanding the sociopolitical configurations of policy proposals. This section is followed by one that introduces the three sets of digital identity principles analyzed in the paper including the reasoning behind their inclusion in the study. Each framework is then analyzed highlighting key elements of their sociopolitical configurations. The paper ends with a discussion of the implications of these configurations for the ongoing development and use of digital identity systems.
2. Previous Research
There is a long tradition of research that builds on the premise that reality is socially constructed through human interpretations, experiences, actions, and the social negotiation of meaning (Berger and Luckmann, Reference Berger and Luckmann1966; Bloor, Reference Bloor1983), particularly emphasizing the role that language plays in this construction (Wittgenstein, Reference Wittgenstein and Anscombe1956; Searle, Reference Searle1995). Whilst such social constructivist research has been applied in many areas, there is a distinct body of research that looks at the social construction or shaping of technological systems (Bijker et al. Reference Bijker, Hughes and Pinch1987; MacKenzie and Wajcman, Reference MacKenzie and Wajcman1999).
These social constructivist insights raise important questions for the development and maintenance of institutional arrangements and systems (Orlikowski and Barley, Reference Orlikowski and Barley2001; Kallinikos, Reference Kallinikos, Avgerou and Land2004). A distinct branch of research extends these ideas to explicitly consider the processes by which social constructivism shapes the implementation of technologies and technological systems (Bijker and Law, Reference Bloor1992; MacKenzie and Wajcman, Reference MacKenzie and Wajcman1999), with many studies drawing on the concept of technological frames.
2.1. Technological frames
Technological frames were introduced by Bijker (Reference Bijker, Bijker, Hughes and Pinch1987) in his study of the development of bakelite as a commercially viable synthetic resin by Leo Baekeland. For Bijker, technological frames refer to the ways in which relevant social groups (or stakeholders) attribute various meanings to an artifact (Pinch and Bijker, Reference Pinch, Bijker, Bijker, Hughes and Pinch1987). As such, the frames are located “between actors” (1987, p. 172) and relate to the interaction of various actors.
The (potentially) different technological frames of each social group help explain the subsequent evolution of the artifact. For example, the successful development of bakelite, according to Bijker, built on the technological frame of earlier Celluloid based research as well as Baekeland’s inclusion in an electrochemical technological frame. This alternative frame enabled him to undertake a systematic investigation of the factors bearing on the chemical reactions he was using (1987, pp. 170–171).
Bijker’s approach has been extensively adapted to show how technological frames shape the development of information systems (Orlikowski and Gash, Reference Orlikowski and Gash1994). For example, one study examines the determination of requirements for new information systems (Davidson, Reference Davidson2002). That paper looks at the requirements determination process and technological frames act to direct attention and to filter out contextual information inconsistent with the existing worldview of the developers.
Similarly, Lin and Silva (Reference Lin and Silva2005) see technological frames as a “cognitive device that enables individuals to comprehend, understand, and explain the world around them. Individuals rely on frames to make sense of their world” (2005, p. 50). As a consequence, they find that successful implementation of an information system will be facilitated by achieving congruent technological frames, adding that these understandings, interpretations, and expectations of information systems are “framed and reframed through the exercise of power” (2005, p. 58).
Guenduez et al. (Reference Guenduez, Mettler and Schedler2020) apply technological frames to public administration in relation to decisions as to whether to use big data analytics. They find that there are both incongruities between the frames used by different stakeholders and shared thought patterns across groups. One consequence is that if these similarities and differences are not articulated or discussed, they can often result, sometimes unintentionally and unknowingly, in misaligned expectations or even contradictory actions. In development contexts, where resources and capabilities can be in short supply, misaligned and contradictory actions between relevant social groups can be incredibly wasteful and perpetuate inequalities (Martin and Taylor, Reference Martin and Taylor2021).
2.2. Expectations and imaginations
A related literature examines the role of imagination and expectation in shaping the development and adoption of new systems (Brown and Michael, Reference Brown and Michael2003; Borup et al., Reference Borup, Brown, Konrad and Van Lente2006). This research seeks to “engage with the future as an object of critique in its own right, refraining entirely from attempts to predict or envisage the future of today’s emerging innovations” (2003, p. 5). It shows that “expectations may be seen to exhibit certain material and social path dependencies (lock–in or irreversibility) becoming the basis for future envisioning, a predisciplining of the imagination through the legacy of former expectations” (Borup et al., Reference Borup, Brown, Konrad and Van Lente2006, p. 293).
Thus, for Berkhout (Reference Berkhout2006), “expectations are inscribed into all social and political action… This is especially the case for activity that sets out to be innovative, where the intention is to act on the world and to change it” (2006, p. 299). He notes that expectations and visions (cf. Swanson and Ramiller, Reference Swanson and Ramiller1997) can take many forms including entirely private, tacit and unformulated phenomena as well as “visualised, disseminated and debated ideas” such as the digital identity principles studied in this paper.
Berkhout suggests that such imaginary future visions have three characteristic features: objectives which are the qualitative or quantitative expression of novel future outcomes; orders which are a set of social and institutional relationships in which these objectives can be met; and technologies which are the means for achieving objectives (2006, p. 302). These three features can play a number of roles in systems innovations including for mapping a “possibility space” or as a stable frame for target setting and monitoring progress. They can also play a role in bringing together various stakeholders such as symbols, narratives, and moralities that bind together communities of interest and of practice and, more generally, as a narrative for bringing together and focusing resources (capital, knowledge, networks, skills, etc.). He also explicitly links expectations and imaginations with framing that points “to the technical, institutional and behavioural problems that need to be resolved in order for a particular vision to be realised” (2006, p. 305).
2.3. Developmental discourse
Literature on international development also highlights the importance of ideas and imagination in shaping the goals and aspirations of efforts to enable change and progress. However, this literature that explores efforts to enable planned or intentional processes often also includes interrogation that focuses around the imagined goal of such efforts to ask “What is intended by development?” (Cowen and Shenton, Reference Cowen and Shenton1996, p. xiii). Highlighting the importance of individual and institutional power, it also asks a further question: “Who decides what development should be?” (Crewe and Axelby, Reference Crewe and Axelby2013, p. 4). Such questions inform the exploration of development doctrines in general, as well as the interrogation of “assumptions on the nature of ICT innovation and on the way such innovation contributes to development” (Avgerou, Reference Avgerou2010, p. 1) or whether ICT is actually a force for good that does not cause harm to disadvantaged people (Masiero, Reference Masiero2022).
While until recently there was limited attention to the notion of what constitutes development in studies of information and communication technologies (Masiero, Reference Masiero2022), there has been a drive, in part by the post or decolonialist turn in studies of information and communication technologies in development, to emphasize the importance of paying attention to alternative perspectives on notions of development and innovation (Santos, Reference de Sousa Santos2014; Wyse, Reference Wyse2015; Jimenez and Roberts, Reference Jimenez, Roberts, Nielsen and Kimaro2019). This literature highlights the importance and insight to be gained from critically examining the expected goals and standards of development interventions.
2.4. Sociopolitical configurations
Taken together, these literatures on technological frames, expectations, and imaginations and developmental discourse describe what this paper calls the sociopolitical configurations that lie behind various interventions, such as the digital identity principles explored below. These configurations are neither good nor bad, but also never neutral—they necessarily embody a subtle politics that ought to be carefully examined, especially to help identify gaps and assumptions and their consequences for development.
Technological frames introduce the notion of relevant social groups. For the digital identity principles studied in this paper, the main relevant groups are the authors and sponsors of the principles. However, there is no guarantee that the technological frame of this group is congruent with the technological frames of other relevant social groups, including policy makers and implementation entities. Thus, drawing on insights from developmental discourse it is important to question what form of developmental goals are implied by the principles (and the group that produced them) and how open they are to alternative perspectives on notions of development and innovation from other relevant social groups.
From the perspective of the expectations and imaginations, this questioning also applies to consideration of the objectives of the digital identity principles, the social and institutional orders within which they can be met as well as their narratives for bringing together and focusing resources. Finally, the questioning continues in relation to the technologies which are seen to be the means for achieving the objectives.
These elements are summarized in Table 1 and are the means by which the paper operationalizes Renieris’s exhortation to contest the underlying imaginations that shape any given technological system. The table combines analytic categories from the literature on technological frames and expectations and imaginations with developmental discourse to generate a series of questions that enable us to explore, as Renieris suggests, the implications of the imaginations the digital identity systems documents represent.
Table 1. Sociopolitical configurations
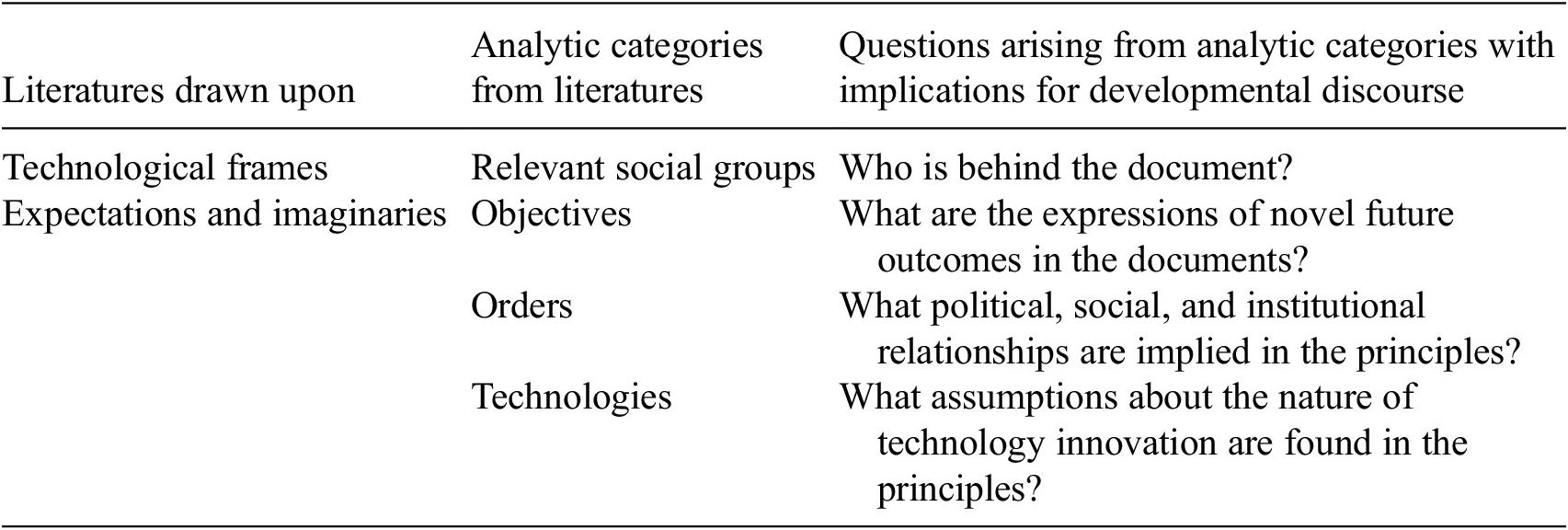
3. Three Digital Identity Documents
The paper explores the sociopolitical configurations of three documents proposing principles for the development of digital identity systems. These were published in the 5 years following the launch of the SDGs including SDG 16.9. The documents are the World Economic Forum’s (WEF) “Identity in a Digital World: A new chapter in the social contract” (2018), the document “Digital Identity: Towards Shared Principles for Public and Private Sector Cooperation” (2016) produced by a team from the World Bank, GSMA (the mobile industry’s member organization) and the Secure Identity Alliance (an identity industry association) and Access Now’s letter calling on the leaders of international development banks, the United Nations, international aid organizations, funding agencies and national governments: to question “Why ID” (2020). Access Now is a nonprofit with a mission to defend and extend the digital rights of people around the world.
These three documents were chosen to represent three distinct worldviews and approaches to digital identity. They were selected as lead representatives of independent international organizations supporting a new social contract between individuals and institutions in a digital world, public and private sector cooperation and civil society. The titles of each document indicate the diverse worldviews that drive them: social contracts, public–private cooperation, and even questioning the assumptions of identity systems.
Although the authors of this paper have contributed to the development of other sets of principles in this space (e.g., World Bank, 2021b), these three documents were chosen for their distinctive perspective on the development of digital identity systems to address SDG 16.9. Additionally, the research does not focus on the consultative processes by which the documents were agreed; instead, the focus is on the resultant documents as these are the items that will be used by policy makers in the digital identity space. While each document is produced by a range of stakeholders, the paper assumes whilst there may be a congruence of understanding around the resulting document, the underlying worldviews of the individual stakeholders will remain distinct.
The “WEF” document is an “insight report” and emerges from a meeting of “public and private stakeholders” interested in digital identity. The document was produced with the support of the management consulting firm Accenture and aims to advance digital identity that is “good for business, government and society.”
For convenience, we label the second document as the “GSMA” document. The GSMA’s digital identity work was undertaken as part of the M4D (Mobile for Development) initiative, a not-for-profit unit of the GSMA. In terms of digital identity, it seeks to enable digital identity “through the power of mobile” (Mobile for Development, 2022). Other contributors to the document were members of the World Bank ID4D team and identity industry association Secure Identity Alliance.
Finally, the “Access Now” document was chosen for its explicit representation of “civil society organisations, technologists, and experts” working on digital identity. Access Now is a civil society organization with a track record of highlighting the harm caused by digital technologies and advocating for the rights of individuals.
3.1. World economic forum
The “WEF” document describes itself as a publication that reflects the collective insights of public and private stakeholders committed to shared cooperation around digital identity intended for “decision–makers and practitioners.” The document “takes stock of where we are today and identifies gaps in coordination across sectors and stakeholders. It outlines what we have learnt to date on what user centricity means and how to uphold it in practice. It attempts to offer a shared working agenda for leaders: an initial list of immediate–term priority actions that demand cooperation. It reflects, in short, the first stage in collective learning and the creation of shared goals and paths” (2018, p. 4). The document, in other words, aims to reflect on the state of the field of digital identity and to outline a framework for what “good” digital identity should look like.
The document consists of four chapters—with the first outlining the importance of digital identities, the second exploring what “good” digital identity looks like along five dimensions of value to individuals, the third is forward looking and describes the opportunities and challenges that arise from the widespread use of digital identities. Chapter four concludes with six priority areas for public–private collaboration in support of digital identities.
The document describes identity as something that is both individual—“personal history, innate and learned beliefs” (2018, p. 9)—and also social—“a bundle of cultural, family, national, team, gender or other identities” (2018, p. 9). Nevertheless, throughout the document, the importance and value of digital identity are overwhelmingly framed as something primarily of individual value, even when discussing the social contract between the individual and the state.
This is seen, for example, in how identity is related to individual rights: “how individuals are represented in society has been the bedrock for reimagining and renegotiating the rights, freedoms and responsibilities of individuals and the organisations to which they relate” (2018, p. 9) continuing that “Any discussion on shaping digital identities should start and end with the individual” (2018, p. 9 emphasis added). “What good looks like” is based on values “that respect individual freedoms” (2018, p. 9 emphasis added). Moreover, the document defines the five elements of “Good ID” as fit for purpose, inclusive, useful, offers choice and is secure (2018, chap. 2). All of these are framed in terms of the value they offer to individuals.
However, despite claiming that any discussion on shaping digital identities should start and end with individuals, the document also makes claims about using digital identity to create value for business and governments as well as individuals: “For businesses, verifiable identities create new markets and business lines, better customer experiences, improved data and a tool against fraud. For governments, they offer a new way of governing: better delivery of services, a more engaged citizenry and a tool against corruption and crime” (2018, p. 10).
This tension between the value that accrues to the individual compared to the value that accrues to the system owner was noted by Crosby (Reference Crosby2008) who proposed identity assurance as “a consumer–led concept, a process that meets an important consumer need without necessarily providing any spin–off benefits to the owner of any database” (2008, p. 3) whereas for more traditional identity management systems the benefits accrue to the system owners.
Interestingly, almost all the examples of real-world identity systems quoted in the document (BankID in Sweden, NADRA in Pakistan, UNHCR’s refugee ID, Aadhaar in India) are ones which can be seen primarily as initiatives that are of value to issuing institutions/owners of the identity database. For example, Aadhaar was promoted as addressing leakages in various social welfare schemes (Bhatia and Bhabha, Reference Bhatia and Bhabha2017), the work of UNHCR seeks to manage refugee populations on behalf of nation states (Martin et al., Reference Martin, Sharma, Peter de Souza, Taylor, van Eerd, McDonald, Marelli, Cheesman, Scheel and Dijstelbloem2022).
The document includes an appendix detailing design considerations for practitioners which is focused on designing and constructing user-centric systems that are useful, inclusive, secure, fit for purpose, and offer user choice and control.
3.2. GSMA
The “GSMA” document “explores the connection between digital identity and sustainable development” (World Bank et al., 2016, p. 7). Consisting of three parts, the first part explores the opportunities of digital identity as well as the challenges to realizing those benefits, the second outlines the “digital identity lifecycle” and design considerations while the third part concludes by proposing some common principles for “unlocking the value of digital identity.”
For the GSMA document, what is meant by value is taken from an earlier report (GSMA and Secure Identity Alliance, 2014) which talks about digital identity unlocking the potential of the digital economy. That document sees the economic value of identity in terms of how identity systems help the economy function effectively, where services such as automation, tax collection, and digital signatures are just some of the ways that governments across the globe can save money (2014, p. 6).
In the main GSMA document, identity is framed as a key to inclusion and its absence to exclusion. The document argues that the private sector has an important role to play resulting in “evolving models of public–private partnerships to build and strengthen identification in poor countries” (2016, p. 10 emphasis added), with a key role for “private sector innovations in new technologies to strengthen the ability of remote or vulnerable populations to access key services” (2016, p. 10 emphasis added).
The GSMA document identifies the “identity gap” as the main issue limiting the potential of digital identity to realize promised benefits, arguing that identity exclusion leads to exclusion from other services, benefits, and entitlements. It argues that the private sector has a key role to play in bridging this gap to realize the benefits of digital identity. Given the interests of the industry associations contributing to the document, it is unsurprising that the document argues that the private sector has an important role to play in advancing inclusion. It is also important to acknowledge that the private sector’s primary goal is profit and shareholder value. With contributors to the report coming from a unit that sees its mission as leveraging “mobile technology as an enabler of digital identity and associated services which provide social and commercial value in developing markets” (Mobile for Development, 2022 emphasis added) and mobile operators often partnering with countries in the developing world and leveraging their nationwide network to help increase access and inclusion at reduced cost, it is perhaps unsurprising that the document also suggests that successful initiatives depend on the private sector partnering with governments to ensure the resulting systems are “effective, secure, inclusive and trustworthy” (2016, p. 10).
The document also emphasizes the political economy of change, noting that existing identity systems will have vested interests that may be resistant to change and that in order to overcome this there is a need for a “unified vision and approach that can overcome the common fragmentation of identity by ministries, departments, regions, or donor funded projects related to identification” (2016, p. 14). There is thus an acknowledgement that the private sector is not positioned to resolve these issues and an implicit suggestion that private sector companies do not themselves contribute to this fragmentation as there is no recommendation for how the private sector can also play a role in resolving it. Despite this, some donor funded projects that work with mobile operators may produce sector specific fixes that institutionalize the fragmentation.
The document also notes that “creating a digital identity system is a costly project that may require extensive investment in building or updating infrastructure and technology” (2016, p. 15). The ICT for development literature recognizes that “top–down, technology–centric, goal–diffuse approaches to ICT contribute to unsatisfactory development results” (Dodson et al., Reference Dodson, Sterling and Bennett2013, p. 19) yet the document argues for investment in building or updating infrastructure includes “strategies to reach remote areas and ensure ‘last mile connectivity’” (2016, p. 15), although nonmobile phone and offline alternatives are also in scope. In other words, technology remains at the core of the document’s argument for the role of digital identity technologies in international development, for example, noting that “mobile technology is uniquely positioned to enable accessible and inclusive digital identity” (Mobile for Development, 2022 emphasis added). Other approaches in the international development policy and literature promote a “holistic model of civil registration, vital statistics and identity management” which emphasizes a lifecycle approach to registration from birth to death rather than technical measures in and of themselves (UN Legal Identity Expert Group, 2022; Wersum, Reference Wersum2022).
Although the principles of “good” ID are framed in the document in terms of individual value, overall the document is dominated by discussion of institutional value and technologically led interventions. For example, Table 1 includes a long list of institutional stakeholders and roles whose primary goals are not individually focused but instead highlight institutional benefits such as fraud reduction and consistent identity management.
3.3. Access now
The Access Now document is a critical challenge to the dominant, mainstream discussions around digital identity, written in the form of a letter to which there are over 110 organizational and nearly 200 individual signatories. The short two page letter aims to highlight key concerns and to frame some specific questions that need to be addressed in order to answer the question of “Why ID?”. These concerns are expanded in their detailed review of the Indian identity system, Aadhaar (Access Now, 2021).
The document argues that there is “a generalised assumption that certain kinds of digital identity programmes empower users” but notes that while benefits can be scalable, so too can harms, particularly as “single points of truth” can also become single points of failure or a means “to track and log the everyday activities and transactions of a user” (Access Now, 2020).
The Access New document highlights the importance of being clear about the specific technologies and models of identity schemes, a common critique of many identity system proposals (Whitley and Hosein, Reference Whitley and Hosein2010). The document also flags concerns around specific technologies, highlighting concerns around biometrics specifically, noting that although they have become increasingly popular, they pose greater risks because unlike passwords, “biometric indicators cannot simply be reset or changed as needed.” This can result in greater risk because it “becomes increasingly difficult to repair the damage done by leaks or hacks of biometric data.”
Moreover, the Access Now document notes that all too often assumptions about benefits lack strong “supportive evidence of the promised benefits.” For example, a widely cited report from McKinsey (2019) estimates the value of digital identities to be between 3 and 13% of GDP in 2030. However, the McKinsey report also states that the value estimates “assume the digital ID program enables multiple high value use cases, attains high levels of usage, is established with individual consent, and protects user privacy and ensures control over personal data” (McKinsey Global Institute, 2019, p. vii). It is unclear what benefits will accrue to digital identity systems if not all assumptions are met.
The Access Now document is particularly concerned about the routine deployment of digital identity systems in less developed economies at a time when they have been widely questioned and opposed in other countries (Bennett and Lyon, Reference Bennett and Lyon2008; Lyon, Reference Lyon2009; Whitley et al., Reference Whitley, Martin, Hosein, Boersma, Fonio and Wagenaar2014). Moreover, their de facto mandatory use in many circumstances risks excluding those who are already vulnerable, such as those unable to access supporting identification documents to prove their identity or who have limited access to digital technologies (Khera, Reference Khera2019; Rao, Reference Rao2019; Manby, Reference Manby2021; Martin and Taylor, Reference Martin and Taylor2021) and thus the benefits, services, and rights they function as gatekeepers for. This highlights how digital identification technologies can “amplify’ existing vulnerabilities. This “amplification” effect of technologies in international development is well recognized (Toyama, Reference Toyama2011).
Although both of the previous documents emphasized the need for trustworthiness coupled with effective data protection laws, the Access Now document notes that the surveillance and discrimination risks are accentuated in contexts “with a lack of comprehensive privacy and surveillance frameworks, compromised institutional standards, and weak independent enforcement” (2020). This echoes Kak et al.’s (Reference Kak, Ben-Avie, Munyua and Tiwari2020) concerns about the tendency to “experimentation with tech in low–rights environments” (2020, p. 3).
4. Discussion
There is a sense of fatalistic determinism in the view that “our identity is increasingly digital, distributed and a decider of what products, services, and information we access” (World Economic Forum, 2018, p. 9). As increasing numbers of digital identity systems are being developed and deployed to form the digital infrastructure on which lives increasingly rely, policy makers are looking for guidance and support on how to develop such systems. This need is being met by a range of organizations and institutions advancing specific principles, frameworks, and “imaginaries” of what “good” digital identity looks like.
This paper does not make a stand on which of these proposed principles are the “right ones” but instead seeks to help identify and articulate the relationships between institutional interests and articulated principles. It introduced sociopolitical configurations as a means of studying these underlying worldviews and their implications. Table 2 explores the sociopolitical configurations of the three policy documents using the questions presented in Table 1.
Table 2. Exploring the sociopolitical configurations of the three documents

4.1. Relevant social groups
The stakeholders and social groups behind the three documents have some overlap but are distinct. The WEF document refers to a mix of private and public stakeholders. The document also acknowledges the valuable support of a private sector consultancy firm who acted as project advisers for the document. The GSMA document describes the involvement of diverse stakeholders but stresses the role of the private sector. The Access Now document is shaped by organizations and individuals who focus on the interests of individuals and civil society but has less to contribute to the role of the state in addressing developmental goals. These sociopolitical configurations highlight a stark divide between stakeholders representing a combination of state and private sector organizations and those representing civil society.
A significant implication of this divide becomes apparent in discussions of where the benefits of digital identity systems accrue. Despite the framing of “good identity systems” in terms of their benefit to individuals, there is a tendency for the documents to resort to examples of institutional benefit to demonstrate their utility which is a very different form of developmental impact.
4.2. Objectives
As digital identity systems increasingly confront issues of trust, power, and politics, the articulation of objectives and outcomes of these systems become framed in development terms. The analysis shows a narrative turn to framing digital identity systems and efforts to shape them in terms of individual agency. This appears to be done to ensure the continued support to their deployment by framing the initiatives as contributing to specific values around individual empowerment, agency, and self–efficacy. Where such outcomes are not necessarily the primary goals of all stakeholders—such as the profit and value drivers of the private sector—the documents seek to align the different motives toward these goals and values.
4.3. Orders
The analysis also suggests a disjunct between the orders and relationships implied in the stated goals and the substance of the documents. Even when the principles are framed in terms of “individual” value, all too often they do not act as a meaningful constraint on the relentless push to expand digital identity around the world, where significant benefits might end up accruing to global consulting, technology, and system integration firms (Kak et al., Reference Kak, Ben-Avie, Munyua and Tiwari2020). That is, the principles rarely function as a regulating mechanism over the diverse and competing interests of the various bodies involved, which can be particularly significant in developmental contexts.
4.4. Technologies
The analysis also suggests a strong technological focus, particularly within industry and private sector-driven approaches to digital identification. For example, the WEF document proposes a user-centric identity system and seeks to “empower individuals to make informed decisions about their identity and privacy” (2018, p. 22) but fails to acknowledge the implications of poor quality legal regimes found in many developing countries for enforcing privacy rights and downplays the very real effects of the digital divide.
In contrast, the civil society focus of the Access Now documents emphasizes wider legal and regulatory considerations required to mitigate potential harms arising from misuse of the technologies involved. Furthermore, the focus on technologies excludes consideration of the wider identification ecosystem, particularly the role of civil registration and vital statistics. This is striking given the role of birth registration in SDG 16.9.
5. Next Steps
Through analyzing the sociopolitical configurations of three digital identity principles documents, this paper contributes to further understanding of the underlying worldviews that shape the documents that will be drawn upon by policy makers. The value of this analysis is to clarify the multiplicity of actors, institutions, and interests behind the documents and to explore the alignments between these stakeholders and development in terms of the principles articulated in the documents. There are more documents available and further analysis to be done to better understand the alignment between stated objectives and stakeholder interests around digital identification. This work is a contribution to achieving this clarity of purpose and the imagined world that these new identity infrastructures are helping to establish.
Acknowledgments
The authors would like to acknowledge the contributions and insights from Aaron Martin and Malavika Raghavan. The perceptive comments from the reviewers and editors have helped improve the paper significantly.
Funding Statement
This work received no specific grant from any funding agency, commercial, or not–for–profit sectors.
Competing Interests
The authors have no competing interests in relation to the documents analyzed. E.A.W. contributed to the development of the World Bank led principles on identification and has undertaken other consultancy work for the World Bank ID4D team. E.S. has undertaken roles for the Omidyar Network funded Good ID initiative as well as work for the UK Department for International Development, now part of FCDO, who were one of the funders of the GSMA Mobile for Development work.
Author Contributions
Conceptualization: E.A.W., E.S.; Formal analysis: E.A.W., E.S. Investigation: E.A.W., E.S.; Methodology: E.A.W., E.S.; Writing—original draft: E.A.W., E.S.; Writing—review and editing: E.A.W., E.S.
Data Availability Statement
The analysis is based on publicly available and cited documents of digital identity principles.






Comments
No Comments have been published for this article.