1. INTRODUCTION AND BACKGROUND
Threats, verbal and written, are considered to be pure language crimes (see Storey Reference Storey1995), as they are committed through the act of uttering threatening words or writing them in a letter. The Internet provides plenty of opportunities for anyone who intends to send a threatening message (see Wallace Reference Wallace1999) and based on the International Crime Victims Survey which was administered to more than 300,000 people over the past 20 years, it is estimated that around one-quarter of all threatening communications are sent via some form of electronic device (Spitzberg Reference Spitzberg2002). Further, based on the same survey, it is estimated that approximately 5% of the population world-wide falls victim to threats each year, and that only around 30% of threats are reported to investigative agencies (see Warren Mullen & McEwan Reference Warren, Mullen and McEwan2014:21). Although threats can be frightening for the victim, not all threatened actions are carried out. In fact, threats are often intended only to create fear in the victim; once realized, the need to carry out the threat is obviated. Solan & Tiersma (Reference Solan and Tiersma2005:199) argue that ‘threats that do not instill fear are not likely to be considered crimes’. The aim of instilling fear in the victim has also been discussed by Warren et al. (Reference Warren, Mullen and McEwan2014:20), who state that ‘those determined to attack disadvantage themselves by giving warning via a threat’. Thus, threats may on occasion be an attempt to remove the need for an attack.
Nevertheless, ‘a significant minority’ (Smith, O'Toole & Hare Reference Smith, O'Toole and Hare2012, cited in O'Toole & Smith Reference O'Toole and Smith2014:237) do carry out their threats, which is why ‘all communicated threats should initially be taken seriously because any particular individual may act subsequent to his threat’ (Meloy, Sheridan & Hoffmann Reference Meloy, Hoffmann, Meloy, Sheridan and Hoffmann2008:6). Moreover, ‘a threatener's actions can destroy or permanently alter the target's quality of life and peace of mind’ (Smith Reference Smith2006:55), which is why careful analyses and assessments are required for each threat.
Previously, researchers (e.g. Storey Reference Storey1995, Fraser Reference Fraser1998, Napier & Mardigian Reference Napier and Mardigian2003, Gales Reference Gales2010) have distinguished between different types of threats. Generally speaking, threats have been classified into the following categories: direct, indirect, and conditional. According to Gales (Reference Gales and Chapelle2013), direct threats contain clear language that identifies the target, time, mode, and method. indirect threats, on the other hand, bear linguistic similarities to complaints and warnings, and their interpretation as threats is mostly left to inference. Inherently, indirect threats are the most difficult to assess. The third type, conditional threats, are ‘dependent on the fulfillment of another action’ (Gales Reference Gales and Chapelle2013:2) and may contain very clear descriptions of the target, time, mode, and method. Further, using Fraser (Reference Fraser1998) as a foundation, Solan & Tiersma (Reference Solan and Tiersma2005:198) present four conditions that explain what constitutes a threat: Firstly, the author of the threat needs to express an intention to carry out the threatened action. Secondly, the state that is supposed to be brought about (i.e. the threatened action) must be unfavorable for the victim. This point is crucial, because an utterance describing the fulfilment of a favorable act constitutes a promise rather than a threat. Thirdly, there has to be a clear intention to intimidate the victim through the victim's realization of the author's intention, and fourthly, the threatener must intend to be taken seriously. That is, threats that are uttered jokingly or with a sarcastic tone of voice are unlikely to be meant seriously.
Many threats, such as parents warning their children of punishment, are absolutely legal (Fraser Reference Fraser1998). The current study, however, focuses on illegal written threats that can be made in connection to bribery, extortion, and assault (e.g. in cases of stalking), and thus profoundly affect victims and their quality of life.
In order to be able to help victims who receive threats, it is crucial that the author of a threat is revealed. This can prove difficult since threateners often wish to remain anonymous and therefore attempt to apply some form of linguistic disguise. Although some research exists that addresses the problem of disguise (see e.g. Jöns Reference Jöns1982; Kniffka Reference Kniffka and Grewendorf1992, Reference Kniffka1993, Reference Kniffka and Veronesi2000a; Kämper Reference Kämper1996; Coulthard Reference Coulthard1998; McMenamin Reference McMenamin2002; Dern Reference Dern2006), relatively few studies have investigated the use of specific disguise strategies. For spoken language, it seems an evident conclusion that linguistic disguise ‘can have [a] “considerable detrimental effect” on identifying speakers and speaker characteristics’ (Eriksson Reference Eriksson, Llamas and Watt2010:87, cited in Schilling & Marsters Reference Schilling and Marsters2015:207). Based on my research for this paper, I would posit that a similar effect can be found in written texts if authors deliberately distort their writing style in order to avoid identification. However, much more research into this area is needed.
The main challenges for linguists in this area pertain to identifying disguise and finding information about the author despite the use of manipulated language strategies (e.g. for general references on authorship analysis, see Dern Reference Dern2009; Ehrhardt Reference Ehrhardt, Sousa-Silva, Faria, Gavaldá and Maia2013, Reference Ehrhardt, Felder and Vogel2017; Gfroerer & Ehrhardt Reference Gfroerer and Ehrhardt2014; for demographic profiling, see e.g. Fitzgerald Reference Fitzgerald, Denevi and Campbell2004). Otherwise, the information gathered from a text can misguide forensic linguistic analyses. A related problem is addressed by Juola (Reference Juola2012), who has shown, for example, that it can be difficult to detect the actual author of a disguised document, but that it might be relatively easy to uncover attempts at disguise. It has been suggested that experts should focus on the analysis of grammar and syntax (see Fobbe Reference Fobbe2011:174; Juola Reference Juola2012), as these levels are not easily accessible for manipulation. Other levels, such as the lexical level, are easier for writers to influence consciously. However, even if the author wants to include, for example, lexical mistakes, they have to ensure the comprehensibility of the message, as otherwise their demands or the effect of the threat will be lost (see Fobbe Reference Fobbe2014).
Previous research suggests that it can be difficult for the author of a threatening message to manipulate several linguistic parameters simultaneously and consistently during the process of writing (e.g. Kniffka Reference Kniffka2007, Dern Reference Dern2008, Seifert Reference Seifert2010, Fobbe Reference Fobbe2014). Indeed, Kniffka (Reference Kniffka2007) argues that it is nearly impossible for authors to manipulate all grammatical and orthographical rules consistently during the process of writing. Since the processing capacity of the brain is limited (see Fobbe Reference Fobbe2014), it is a cognitively demanding task to manipulate one's language production convincingly. Normally, processes involved in everyday tasks, such as driving a car or writing a shopping list, are automated in order not to waste too much mental energy. Automatized processes like these do not strain the short-term memory in the brain. These processes, however, are disturbed if the writer intentionally wants to include mistakes in their writings, which is only one of several possible forms of disguise. (Others will be outlined below.) In that case, the writer has to suppress correct spelling, grammar, and word choice, and use incorrect letters, sentence structures, and words. As can be expected, it is almost impossible to use the same amount of attention during the production of a whole text. As a consequence, the number and type of mistakes will likely vary throughout a disguised text (see Kniffka Reference Kniffka2000b, Reference Kniffka2001:169f.; Dern Reference Dern2008:247; Fobbe Reference Fobbe2014:203ff.). Inconsistencies of these types can also be found regarding other forms of disguise, such as the use of dialect or colloquialisms, but these inconsistencies have only been discussed in relation to deliberate mistakes and forms of foreigner talk (see Fobbe Reference Fobbe2011, Reference Fobbe2014).
Average offenders, who seldom write threatening messages or other forms of anonymous texts, cannot be expected to fully master the metalinguistic reflections that are necessary for a successful disguise. For example, Coulthard (Reference Coulthard1998:122) states that
as with any fabrication, be it bank notes or written texts, the quality of the finished product will depend on the degree of understanding that the falsifier has of the nature of what he is falsifying.
For the current purposes, this can be viewed in connection to the imitation of someone else's writing style. If someone intends to imitate someone else's writing style, they would need to have enough linguistic and meta-lingusitic knowledge to be successful. For example, the falsifier would need enough knowledge of their own language patterns, the third party's language patterns whose style is to be imitated, as well as knowledge about the intended text type. That is, if the author does not have enough knowledge of how a threatening message typically looks, they will be unable to falsify it effectively, and if the author lacks knowledge of their own and the other person's writing style, they will be unable to make the necessary manipulations. As will be seen in this paper, the required linguistic and meta-linguistic knowledge for successful disguise is often not present, which is why disguised texts can exhibit inconsistencies.
Disguise comes in many shapes and forms. Research on German texts has shown that the following strategies are possible: inclusion of features of foreigner talk; random mistakes (e.g. spelling); imitation of another person's writing style; anonymization (e.g. the avoidance of self-references or the use of plural personal pronouns in order to pretend to be a group of people rather than a single person); manipulation of spelling, orthography and punctuation; lowering of linguistic abilities in order to pretend to have a low level of education (e.g. masking grammatical and lexical abilities through the inclusion of mistakes); and changes of register (see Dern Reference Dern2008, Seifert Reference Seifert2010, Bredthauer Reference Bredthauer2013, Fobbe Reference Fobbe2014, Marko Reference Marko2016).
Studies by Dern (Reference Dern2008), Seifert (Reference Seifert2010) and Fobbe (Reference Fobbe2014) have shown that people are rarely aware that features of their written texts can point to aspects of their identity. Despite the well-publicized revelation of J. K. Rowling as the author of A Cuckoo's Calling (see Juola Reference Juola2013), awareness of forensic techniques among laypeople is still very often limited to knowledge about handwriting analyses, as will be discussed later in this paper. However, it has also been shown that around 20% of threatening messages do contain cues to disguise (see Bredthauer Reference Bredthauer2013:65) and it is thus important to recognize these cues.
The current paper addresses the question of people's underlying motivation for or against the use of disguise in written threatening communications. Through the use of two separate studies, the following research questions are addressed: (i) How is the form of disguise related to awareness of language and writing style, and to what extent is this awareness reflected in the motivation for disguise? (ii) Are there culture-specific differences related to the use of disguise and the perception of threats between American and Austrian participants?
2. METHOD AND DATA
Parts of the results elicited in a larger dissertation project were combined in order to answer the research questions posed above. The dissertation project aimed to investigate disguise strategies and also yielded interesting findings regarding the participants’ motivation for disguise. The design of the present experiment is based on previous experiments conducted by Dern (Reference Dern2008), Seifert (Reference Seifert2010) and Fobbe (Reference Fobbe2014). The current design differs from Dern's (Reference Dern2008) and Fobbe's (Reference Fobbe2014) in two main aspects: Firstly, the participants were not prompted to use a specific form of disguise (e.g. foreigner talk; see Fobbe Reference Fobbe2014), and secondly, they were asked about their decision for or against the use of disguise. An experimental design such as the one used in the present study has the advantage that background information about the individual participants can be collected and used for the interpretation of the results. In authentic threats, the actual authors are not always known, and additional writings by the same person are rarely available for enabling comparisons of writing style. Of course, an experimental design also has its limitations, which will be discussed later in this paper (see Section 3 below).
In the first experiment, the participants were asked to write a threatening message themselves and were not instructed to apply any form of disguise in their writings. After they had written their text, they were asked whether or not they had tried to alter their ‘normal’ writing style and how they had done so. Additionally, they were asked to write an informal e-mail in their ‘normal’ writing style in order to produce a text sample for comparison. The participants were provided with two different but informal topics (plans for the weekend or recent vacation) from which to choose. These two options were provided in order to enable participants to choose a topic with which they felt more comfortable. Of course, this could lead to different writing styles, but the informal writings were not compared with each other – they were compared to the respective threatening message or ransom demands. In the second study, a different group of respondents were asked for their views on threatening messages and disguise (e.g. whether they thought disguise was common, and how and under which circumstances people would or would not manipulate their writing style), and their own experiences with such texts. Table 1 illustrates the most important information about the participants in both studies.
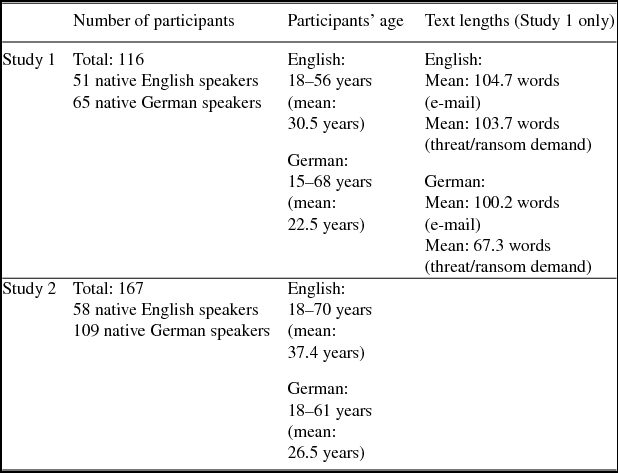
Table 1. Participant and text characteristics.

The first study contained texts and responses from 116 participants (51 native English speakers, mostly from the United States, and 65 native German speakers, mostly Austrians), while the second questionnaire yielded answers from a total of 167 respondents, 109 of whom are speakers of German (mostly Austrians) and 58 are speakers of English (mostly from the United States). The German-speaking participants’ texts contained 100.2 words (e-mail) and 67.3 words (threat/ransom demand) on average, while the English-speaking participants’ contained a mean of 104.7 words (e-mails) and 103.7 words (ransom demands/threats). The English texts were thus slightly longer than the ones produced by the native speakers of German (e-mails: p = .055; ransom demands: p = .003).
The data for both studies were collected through online questionnaires (see Appendix) that were distributed using the snowball system, which means that each participant passed the study on to others, as well as through social media platforms. This, of course, can lead to a selection bias, in that only people with similar backgrounds and interests choose to participate in the study and pass it on to people in their network. However, by sending out the questionnaires to a variety of people known to the author who had different social and demographic backgrounds and asking them to pass on the questionnaire to people of different ages and with different socio-economic backgrounds, the author tried to ensure that respondents of a variety of backgrounds were included. The participants provided answers voluntarily and could withdraw from the questionnaire at any time if they wished to do so.
3. RESULTS AND DISCUSSION
The main findings for each study will be outlined and discussed separately, followed by a discussion of the common implications of the findings of both studies. First, however, some limitations of the current studies are outlined.
3.1 Limitations
The first limitation of the data used in this study is due to the fact that the threatening messages were produced solely for the purposes of this study, which means that the participants may not have felt the need for disguise in the same way they would have in an authentic situation. This way, however, it was possible to collect background information about the participants and to ask them additional follow-up questions. Another limitation is the length of the texts: With slightly more than 100 words on average, the texts are rather short. Often, though, authentic forensic texts are hardly any longer and the main problem with the short texts applies mostly to quantitative analyses rather than qualitative ones. The data was collected through the snowball system, as mentioned previously, which can lead to selection bias in that only people who have a default interest in the topic or know each other would participate. With these limitations in mind, I will now present and discuss the main findings of the two studies.
3.2 Study 1
An analysis of the participants’ answers to the open-ended question about what they had changed in their threatening message or ransom demands compared to their informal e-mail revealed that the most commonly mentioned forms of disguise were anonymization (i.e. the omission of personal references as well as the misleading use of plural personal pronouns we/wir, us/uns and our/unser), orthographic changes (mostly capitalization, but also an alternating use of upper and lower-case letters), and changes in register (i.e. the use of an informal register, for example through the use of informal vocabulary or contractions, or the use of a formal register through the use of formal vocabulary, technical terms, and the absence of contractions). Table 2 shows the categories that were composed on the basis of an analysis of the participants’ comments and their frequencies of use.
Table 2. Motivation for disguise mentioned by participants, Study 1. Shading in cells marks the most common strategies.
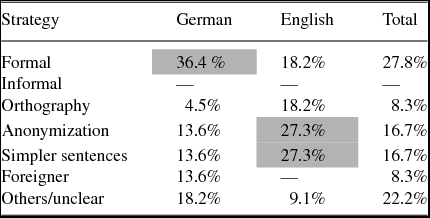
Table 2 shows that the main strategy for the use of disguise mentioned by the German-speaking participants was to sound more formal (36.4%) and thereby use a higher register. For the English-speaking participants, however, a different theme emerged: their main strategy was to anonymize their texts (27.3%) and they wanted to use simpler sentences (27.3%), which can also have a different implication, such as pretending to have a lower level of education (e.g. Dern Reference Dern2008, Seifert Reference Seifert2010). Such conclusions, however, cannot be drawn from this data set. Interestingly, none of the participants stated that they had used a more informal register in their threatening letter, which contradicts previous findings (Seifert Reference Seifert2010). It is also interesting that only the German-speaking participants stated that they had deliberately used some kind of foreigner talkFootnote 1 in their threats, while none of the English-speaking participants did.
Several participants also provided explanations about what they did when they disguised their writing style, yet the answers are relatively unsystematic and mainly refer to the desire of remaining anonymous. The vast majority of participants (86.1%) did not comment on their use of disguise at all. This, however, does not mean that they did not manipulate their language, as the comparison of both texts (the informal one and the threatening message) revealed that 40% of the texts show altered writing styles, even though only 20% had reported to have made changes to their writing style. This is consistent with Bredthauer's (Reference Bredthauer2013:65) findings in her corpus of authentic threatening messages. Below, the answers exemplify participants’ comments on how they tried to change their writing style and what their motivation and/or aim was to use disguise in the first place:
(1) ‘I tried to make it mean and demanding’
(2) ‘I kept it vague’
(3) ‘I intentionally tried to sound ominous, eery, and anonymous’
(4) ‘With shorter sentences’
(5) ‘More professionally’
(6) ‘I used fairly generic language’
(7) ‘Ich habe eine Sprache verwendet, die meiner absolut nicht ähnlich ist’
(‘I have used a language that is not at all similar to mine’)
(8) ‘Ich schreibe „offizielle“ Briefe generell etwas anders, als ich im Normalfall spreche’
(‘In general I write “official” letters slightly differently to how I normally speak’)
(9) ‘Möglichst normal’
(‘As normal as possible’)
(10) ‘Entschlossen und bedrohlich’
(‘Determined and threatening’)
(11) ‘Spezielle Wörter’
(‘Specific words’)
These comments show that although the participants had a general idea that they were trying to manipulate their writing and move away from their normal writing style, they did not have the required level of reflection to indicate what that means. For example, the comment ‘I tried to make it mean and demanding’ (comment (1)) does not indicate how the writer attempted to reach the goal of making a text sound ‘mean and demanding’. Further, it is unclear what it means to the writer to make a text sound ‘ominous, eery, and anonymous’ (comment (3)).
Another example will demonstrate what these comments already show. One of the native speakers of German indicated that he deliberately included a high frequency of dialect words, colloquial language, and spelling errors. Further, he stated that, ‘It would be stupid to write such a letter in perfect German’. Upon a closer look at his normal writing (in his e-mail) and his threatening letter, however, two counter-indications emerged: First of all, he had used a similar amount of colloquial language and dialect in his normal writing, despite indicating the use of dialect and colloquialisms as being a form of disguise. Secondly, although he mentioned the inclusion of spelling errors, no misspellings could be found, except for a lack of capitalization. Rather, he had used dialect words, which may deviate from the standard in regard to spelling but cannot be counted as actual spelling mistakes. For example, a spelling mistake in English would be giong instead of going, but gonna would not be counted as a misspelling. Below, the two German texts are provided for illustration (each followed by my English translation; all underlined words are dialectal, informal, or non-standard):
Text (1a) (normal writing)
Seas Hias, i würd dir ja sehr gern die pläne für mei wochenende beschreiben, nur leider weißt ja eh dass i ma im fuß des dumme bandl grissen hab und i dadurch a bissl viel behindert bin.. najo anywho, wollt di eigentli fragen ob du zeit hast, kommst vorbei, koch ma was feines (enteenteenteente?:D) und dann könnt ma a runde n64 zocken. oder du nimmst dei wiiu mit. shotgun aufn normalen controller.. und nimm meinen kleinen heli wieder mit, i vermiss den scho.peace out
‘Hey, Hias, I would like to tell you about my plans for the weekend, but unfortunately, as you know, I have a torn ligament in my leg, so I'm quite handicapped.. well, anywho, I wanted to ask you if you have time to come over, we could cook something nice (duckduckduck?:D) and then we could play n64. or you bring your wiiu. shotgun on a normal controller.. and bring my small copper, I miss it already. peace out’
Text (1b) (ransom demand)
Wenns euan klan Egon wiedasehn wuits, nemts 100000 Euro in Zehna scheinen und tuats as in an Briefumschlog und den weafts dann im Park in den Mistkübl genau durt wo i auf da Kortn untn des einzeichnet hob und zwoa genau in 3 Tog um 4 in da Fruah. Kane Kiebara.
‘If you want to see your little Egon again, take 100,000 euros in 10-euro notes and put them into an envelope that you throw into the trash can in the park, exactly where I have marked it on the map below, in exactly 3 days at 4 in the morning. No police.’
The German versions of the texts contain similar amounts of dialect features and colloquialisms – at least there is no considerable increase in the ransom demand. This shows that the author is unaware of the extent to which he uses dialect and colloquialisms in his normal writing.
Some participants’ responses, on the other hand, do show that the authors had a specific idea for disguise in mind. For example, comment (4) (‘with shorter sentences’) indicates that the author reflected on their writing style and deliberately tried to change at least one aspect of it. This, however, cannot be upheld upon a closer look at the English-speaking individual's texts:
Text (2a) (normal writing)
My recent trip to Dubai was awesome! The weather was warm and the city reminded me of Los Angeles. It made me miss my old life. We went to the water park. So fun!!! We also took a tour to the Arabian desert. I got a little nauseous driving over those sand dunes. At the end, we could even do some sand boarding. I've always wanted to do that! And we ate way too much on this trip! Of course, we also went up the Burj Kalifa. It was not as great as we expected. Probably just because it was so crowded. Overall it was the perfect place to escape the cold weather!
Text (2b) (ransom demand)
To the manager of the ABC grocery store: Place $100,000 in $20 bills under the large rock at the corner of Western and Main Street at midnight on Sunday. If not – there will be poison in one of your food items. Same of [sic] you involved the police.
As mentioned above, the author of these two texts stated that she used shorter sentences in the second text in order to disguise her normal writing style. However, at a closer look it is obvious that the sentences in the second text are in fact longer than in the first one (a mean of 8 compared to 12 words per sentence). This shows that although the author had a strategy, she was unable to implement it successfully.
Moving back to the textual samples, the participants’ answers, such as comments (5) (‘more professionally’), (7) (‘I have used a language that is not at all similar to mine’), and (11) (‘specific words’) indicate a certain reflection on language use, yet they still exhibit vagueness and imprecision. For example, it is unclear what exactly it means to the participant to make their writing style ‘dissimilar’ to their own (i.e. what changes they would make) or which ‘specific words’ they used that do not leave idiolectal traces in the text. That is, it is unclear whether the participants actually managed to change the aspects of their writing style that they had intended to change (see texts samples above).
Table 3 shows the investigated linguistic features and whether they were found to be statistically different in the two text types (values smaller than .05 show statistical significance in t-tests carried out with SPSS 22; they are set in gray-shaded cells in the table for easier visibility). It can be seen that, for example, the use of adverbs was significantly different in the texts, while the use of commas remained fairly stable.
Table 3. Differences between informal e-mails and threatening messages. The values in shaded cells are statistically significant.
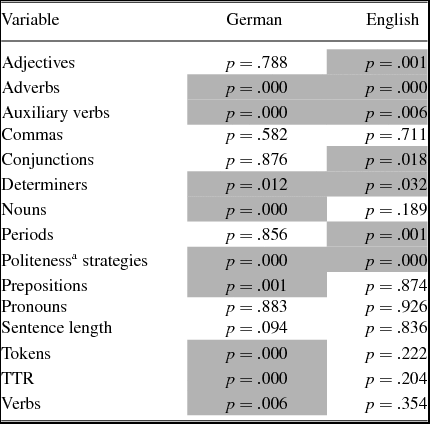
a Regarding politeness, it was investigated whether the texts contained formal forms of address, or instances of positive politeness (e.g. hedges), or negative politeness (e.g. apologies) (see Leech Reference Leech2014).
3.3 Study 2
In the second questionnaire, respondents were asked to provide their opinions of and experiences with threats and disguise. They had to answer questions regarding their own experiences with threats, their experiences with and opinions on linguistic disguise, and their ideas and awareness of language and identity, i.e. whether they were aware of the connection between language and identity. Their answers were then analyzed to see whether the respondents were aware of the connection between language and identity, and how far such awareness (or lack thereof) influenced their opinions on the use of linguistic disguise.
Several respondents in the second study provided interesting answers as to why or in what situation it would be necessary to use any form of disguise at all. Below, randomly selected answers illustrate this.
(12) ‘It would depend on whether they think the person would recognize them if they wrote normally or not’
(13) ‘If someone frequently speaks or writes with a certain form. They may attempt to change their methods of communication and their language to reduce their appearance of being a possible suspect. They may use foul language if they normally talk politely and may be polite if they normally are a vulgar person’
(14) ‘It depends on the desired outcome’
(15) ‘Nein, wenn sie diese am PC verfassen’
(‘Not if they write them on a computer’)
(16) ‘Kommt auf den bisherigen Schreibstil an’
(‘Depends on the writing style up to this point’)
(17) ‘Nur wenn der Empfänger den Absender kennt’
(‘Only if the recipient knows the sender’)
(18) ‘Sprache ohne Auffälligkeiten’
(‘Language without conspicuousness’)
Many answers point to respondents connecting means of disguise with handwriting. Further, some answers also show a lack of awareness of leaving linguistic marks in a text that can be developed into a linguistic profile, even if the author is unknown by the analyst. For example, the respondent answering that someone would disguise their writing style ‘only if the recipient knows the sender’ (comment (17)) displays exactly this kind of unawareness. In other words, it shows that the respondent is aware that something identifiable could be left in linguistic traces, but not that some of such traces may be detected by someone who is not familiar with the writer.
Other answers, such as ‘language without conspicuousness’ (comment (18)) exhibit imprecision and vagueness, which is comparable to the answers given in the first study (‘I tried to make it mean and demanding’, in comment (1) above).
The majority of the questions used in the second study were multiple-choice questions with some possibilities to provide comments. The possible answers for the questions were based on the findings of the first study and on the literature review. The analysis of the comments on the question of which strategies the respondents think people are likely to use as a form of disguise yielded interesting ideas about the perceived underlying motivation for disguise: The vast majority (77.8%) of comments related to the expected desire of threateners to remain completely anonymous (e.g. as opposed to imitating someone else's writing style, where it is the intention to be recognized as a specific third party), while the other 22.2% of comments could not be clearly classified because they were too vague (e.g. ‘Depends on the normal writing style’ and ‘Depends on their motive’).
A theme that emerged, though, was that there seems to be an inherent connection between disguise and handwritten letters, as hinted at above. It was frequently indicated that the use of capital letters, writing with the opposite hand, and typing the letter on a computer would be useful forms of disguise. These, however, are only useful when the text is handwritten or when the respondent thinks that only handwriting can deliver hints about the author, as none of these strategies, such as the use of capital letters, would distort the actual language used, but only its outer form. This is another sign of low linguistic awareness and of the clues that linguistic variation leaves behind.
A few differences between the two investigated groups (English-speaking Americans and German-speaking Austrians) emerged in their responses on what they thought were common strategies for disguise. Figure 1 illustrates these findings.
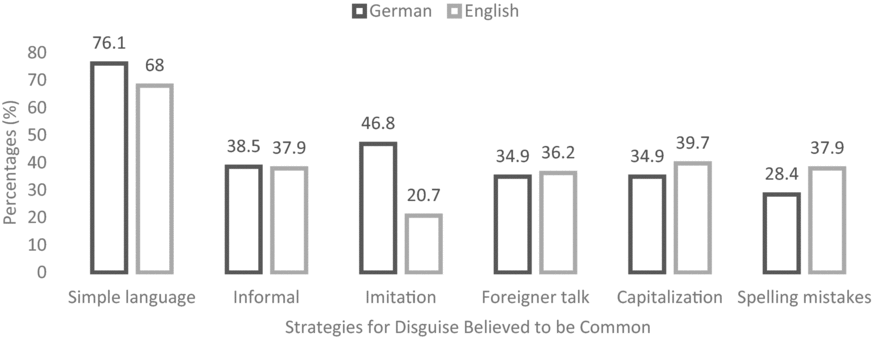
Figure 1. Common forms of disguise.
Overall, speakers of English and speakers of German have similar views about which strategies for disguise are common. The only real exception is the strategy of imitation: more than twice as many speakers of German think that the imitation of another person's writing style is a common strategy for disguise. Interestingly, it is exactly this strategy that demands an even higher linguistic and metalinguistic awareness of one's own and another person's writing style than any other strategy for disguise, if it is to be successful. Thus, this finding illustrates that the actual use and implementation of disguise strategies differs vastly from some respondents’ expectations.
In order to find out whether the respondents only had difficulty expressing their opinions in more accurate ways or whether they also lacked awareness of the existence of clues to a writer's demographic background, they were asked whether they thought it is possible to extract personal (demographic) information about the author from a written text. Figure 2 shows that the vast majority of respondents (98.3% (39.7% + 58.6%) of English speakers and 89.9% (34.9% + 55%) of German speakers) agreed that it is possible to discern some kind of personal information from written texts, i.e. that such information can actually be transmitted through written texts.

Figure 2. Do you think it is possible to collect personal information from a written text?
This finding is interesting in several respects: First of all, it seems that there is a general awareness among the participants that they might leave personal traces in written texts. Secondly, considering that some kind of language awareness exists, the participants in the first study were still unsuccessful in applying linguistic disguise. Thus, even though it is not known whether the participants in the first study exhibited the same level of awareness, this raises interesting questions for further research.
A similar finding that emerged was that 56.9% of the American respondents and 77.1% of Austrian respondents claimed that they would change their writing style in a threatening letter. In the corpus of threats and ransom demands collected through the first study, no numbers even close to these were found regarding the actual use of disguise. This might reflect less on the participants’ awareness of linguistic disguise but more on their ability to apply such disguise successfully.
For the most part, similarities were found between the speakers of English and the speakers of German, but an interesting result regarding the participants’ own experiences with threats emerged: While only 19.3% of German speakers indicated having had personal experiences with threats, 37.9% of English speakers claimed the same. Whether these figures reflect the actual frequency of the occurrence of threats or whether they were caused by different understandings of what constitutes a threat deserves further investigation.
Moreover, it is to be noted that, as Figure 3 shows, 10% of the German speakers and 7% of the English speakers thought that addressees would always take threats seriously, while the largest group (84% of the German speakers and 80% of the English speakers) stated that they thought it definitely depended on the situation whether or not addressees would take threats seriously. A further 6% and 13% of the speakers of German and English, respectively, thought that threats are never taken seriously. This could possibly account for the fact that only approximately 30% of threats are actually reported to investigative agencies (see Warren et al. Reference Warren, Mullen and McEwan2014:21). Looking at the largest group (the 84% and 80% of the German and English speakers, respectively, who claimed that threats are taken seriously depending on the situation), this might indicate that the respondents were aware that threats are often only understood as such in relation to the context in which they are uttered. Speculatively, there might be a connection between whether people think threats are taken seriously and their motivation for or against the use of linguistic disguise in a threat. This, however, would have to be investigated in future studies.

Figure 3. Do you think that the threats in anonymous messages are taken seriously by the recipient?
Along similar lines, 54.1% of the speakers of German as well as 79.3% of the native speakers of English stated that they did not think that authors of threats are likely to follow up on their threats or realize them.
4. CONCLUSIONS
When looking at the results of both studies, it becomes clear that there are many common themes regarding disguise as well as the linguistic awareness of the participants, which in turn influence their motivations for or against the use of disguise in their (elicited) threatening letters or ransom demands.
First of all, this study shows that many people who did use disguise in their threatening messages were unable to reflect on their own writing style and change it in a way that made it fundamentally different from their other writings. That means that if the participants have inaccurate impressions of their normal writing style, they will not be able to manipulate their style thoroughly and consistently enough throughout the production of a whole text to avoid identification.
Further, it appears that for the participants in these studies the word disguise (or the German Verstellung) triggers a connection only to handwritten texts. Aside from explicit mentions of handwriting in both studies, this connection was also implicitly present in the elicited threats, where several participants used only capital letters. This disguise strategy is clearly linked to the manipulation of handwriting (a common form of disguise in handwritten threats), as it does not affect the linguistic choices themselves but only the outer form of the text and therefore does not have much influence on a text written on a computer.
In this connection, as can be expected, respondents in this study demonstrated little-to-no awareness of the possibilities of profiling writers based on sociolinguistic (including dialectal) features of their written texts. Specifically, an awareness that information about an author can be extracted from an (anonymous) piece of writing was not present in the answers the participants provided; nor could it be inferred from their texts. Although some showed slight awareness, for example by stating that it would be odd not to change their writing style in a threatening letter or ransom demand, many only mentioned similar ideas if the recipients knew the authors and were familiar with their writing style.
Finally, this study demonstrates that although many people do have personal experiences with, expectations for, and opinions about threatening messages, these are often unstructured, unsystematic, and vague. This is mirrored in their disguise behavior, which often lacks consistency and results in limited or even unsuccessful implementation of the desired strategy.
To sum up, respondents’ motivation for using disguise seem to be connected to their linguistic and metalinguistic awareness. This linguistic and metalinguistic awareness also influences which disguise strategy is chosen and how successfully the respective strategy will be applied. Research into this area can have implications for the analysis of anonymous texts (e.g. e-mails, letters, text messages) whether or not they contain threats, as well as in the detection of online identity disguise (e.g. in online child grooming).
ACKNOWLEDGEMENTS
First and foremost, I want to thank the participants of both of my studies for their time and effort, without whom this project would not have been possible in the first place. I am particularly grateful for the assistance and support given by my first supervisor, Dr Margit Reitbauer, and for the help received by my second supervisor, Dr Hermine Penz. I also want to thank my parents for their support and positivity throughout this project; and, of course, special thanks are expressed to the NJL reviewers and editors of this special issue for their invaluable input and feedback.
APPENDIX
Excerpt from questionnaire – Study 1 (English version)
(13) Please write a short e-mail (at least 80 but no more than 150 words) to a friend about your plans for the weekend OR about a recent vacation you went on. Please write down whatever comes to your mind – do not give it too much though and keep it as natural and authentic as possible. You do not have to pay attention to correct grammar and spelling.
(14) Now imagine you write an anonymous blackmail or threat letter, which you think could be successful. Address it to the ABC Grocery Store and demand $100,000. Write down whatever comes to your mind and do not think about what to write too much. Feel free to use as many words as you need.
(15) Did you try to disguise your language when writing the ransom demand/threatening letter?
(16) If so, how did you do that?
(17) Is writing something you do frequently? (Multiple answers possible)
Yes, every day
Yes, but not more than once a week
No, never
Yes, because I need it in my job
Rarely
I only write e-mails
I only write text messages
Other:
(18) Do you have any experience with linguistics?
Thank you very much for your help! It is greatly appreciated!
Excerpt from questionnaire – Study 2 (English version)
In this section, ‘anonymous letters’, ‘ransom demands’, and ‘threatening letters’ are not only used in the sense of hand-written texts, but also in the sense of electronic forms of communications, such as e-mails, text messages, etc.
‘Anonymous letters’ or ‘anonymous communications’ are used to include the text types of ‘ransom demands’ and ‘threatening messages’, as the authors of such texts tend to try to stay anonymous.
(7) Do you think that anonymous messages are sent frequently?
Yes, probably on a daily basis
Yes, very often, but not daily
No, not very often
No, rarely
Other:
(8) What kind of people do you think are more likely to send anonymous messages than others? (Multiple answers possible)
Only people with a criminal record/only criminals
Anyone can send an anonymous message
People with other cultural backgrounds/immigrants
People with a low level of education
People with a high level of education
Other:
(9) Do you think that people who write anonymous messages try to disguise their language or style of writing?
Yes, because they want to stay anonymous
No, because no one knows who wrote the message anyway
Other:
(10) Which strategies do you think people apply when they try to disguise their style of writing? (Multiple answers possible)
Simpler sentences/simple language
More complex sentences/complex language
More polite language
Less polite language
Disguise as a foreigner/ /stereotypical language
Imitate a specific person
Spelling mistakes
Capital letters/write in caps lock
Other:
(11) What do you think are most relevant elements of a threatening communication? (Multiple answers possible)
Address/greeting/salutation
Introductory sentence
Threat(s)
Reason for the threat/leverage
Demand(s)
Closing/signature
Introduction of the person writing the letter
Consequences if demands are not fulfilled
Other:
(12) Where do you know about anonymous messages from? (Multiple answers possible)
TV
Books
From real life
Not at all
Other:
(13) Who do you think most threats are addressed to? Who are the recipients? (Multiple answers possible)
Large companies
Companies of all sizes
Banks
Food companies
Private individuals
Educational institutions
People with a (strong) public presence
Other:
(14) What do you think are the most common threats? (Multiple answers possible)
Release of secret information
Bomb threats
Make important information public
Kill someone
Go to the police
Kidnap someone
Poison food
Other:
(15) Have you ever heard of ‘Forensic Linguistics’?
(16) If so, where?
(17) Do you think that it is possible to extract information about a person from a text they have written?
Yes, definitely
Yes, but only to a certain degree
No, probably not
No, absolutely not
Other:
(18) Which of the following information do you think can be found out about the author of a text by analyzing their language? (Multiple answers possible)
Sex/gender
Age
Educational level
Occupation/profession
Regional origin
(19) Which of the following information do you think cannot be found out about the author of a text by analyzing their language? (Multiple answers possible)
Sex/gender
Age
Educational level
Occupation/profession
Regional origin
(21) Have you or someone you know ever received an anonymous threatening message?
(22) Do you think that the threats in anonymous messages are taken seriously by the recipient?
Yes, definitely
Yes, but I think it depends on the situation
No, I don't think so
Other:
(23) Do you think that the authors of anonymous messages are likely to carry out their threats?
Yes definitely
Yes, I think so
No, I think such threats are rarely realized
No, I think such threats are never realized