1. GENERAL INTRODUCTION
According to the Swedish National Council for Crime Prevention (2017), hate crime can be defined as a criminal act in which ‘a person is victimised [in reaction to] their real or perceived ethnic background, race, skin colour or nationality, religious belief, sexual orientation or transgender identity or expression, or for being perceived as representing such a group of people’ (paragraph 3). Using this definition, this crime type encompasses a broad spectrum of biases over a wide variety of offenses. Despite this heterogeneity, one antecedent that hate crimes often share is Anonymous Threat Communication (ATC). As the name implies, ATCs refer to written or verbal messages ‘where knowledge of personal, historical, or clinical factors of the sender is not available’ (Glasgow & Schouten Reference Glasgow and Schouten2014:41). Consequently, hate-crime threat assessment commonly involves ATC analysis.
Though by no means fool-proof, such analysis has been shown to provide useful evidence for predicting and minimizing the risk of inappropriate approach behaviors, including physical violence (Calhoun Reference Calhoun1998, Borum et al. Reference Borum, Fein, Vossekuil and Berglund1999, Fein & Vossekuil Reference Fein and Vossekuil1999, Baumgartner, Scalora & Plank Reference Baumgartner, Scalora and Plank2001, Calhoun & Weston Reference Calhoun and Weston2003, Napier & Mardigan Reference Napier and Mardigan2003, Scalora, Baumgartner & Plank Reference Scalora, Baumgartner and Plank2003). To date, ATC research has identified a number of linguistic features (e.g. thematic content, stylistic format, grammatical construction) and paralinguistic factors (e.g. mode, sophistication, and location of ATC delivery, the relationship between the ATC sender and receiver) with varying degrees of predictive value (Smith & Shuy Reference Smith and Shuy2002, Fitzgerald Reference Fitzgerald2005, Schoeneman-Morris et al. Reference Schoeneman-Morris, Scalora, Chang, Zimmerman and Garner2007, Smith Reference Smith2008, Schoeneman et al. Reference Schoeneman, Scalora, Darrow, McLawsen, Chang and Zimmermann2011, Meloy et al. Reference Meloy, Hoffmann, Guldimann and James2012, Hancock, Woodworth & Porter Reference Hancock, Woodworth and Porter2013, O'Toole & Smith Reference O'Toole and Smith2014, Simons & Tunkel Reference Simons and Tunkel2014).
Within the US, these findings have been used by law enforcement agencies such as the Federal Bureau of Investigation's Behavioral Analysis Unit to develop consistent, transparent, empirically-based procedures for ATC assessment (Miron & Douglas Reference Miron and Douglas1979, Fitzgerald Reference Fitzgerald2005, Simons & Tunkel Reference Simons and Tunkel2014). Explained briefly, this actuarial approach involves systematic empirical evaluation across a pre-determined set of features shown to have both statistical and criminological significance. Through international interagency cooperation, this approach has also been effectively adopted and adapted by European law enforcement and intelligence agencies to assist in the global fight against threatening communication.
One of the challenges of this work is determining what precisely constitutes a verbal threat. Instinctually, most people would contend that threatening is somehow fundamentally different than predicting, promising, warning, insulting, or defaming; and most courts of law would agree. It is for this reason that some of these verbal acts are routinely considered to be lawful and may even enjoy constitutional protections, while others are regularly deemed unlawful and unprotected. Just where exactly the essential differences lie between threatening and non-threatening speech has proven notoriously difficult to discern, even for legal experts (Solan & Tiersma Reference Solan and Tiersma2005; Shuy Reference Shuy2008, Reference Shuy2010; Walton Reference Walton2014; Berk-Seligson & Seligson Reference Berk-Seligson and Seligson2016).
This difficulty is exemplified in the following two constructed utterances:
(1) Keisha, if you move into this neighborhood, I will see to it that you wake up tomorrow to a cross-burning on your front lawn!
(2) If you move here, you might wake up to a nasty surprise!
Example (1) contains many of the characteristics that have been identified as typifying threatening utterances: (i) the addressor expresses personal intent to commit a future negative action [Y] against the addressee; and (ii) the commission of this negative action is made contingent upon the addressee's failure to comply with the addressor's directive [X] (Fraser Reference Fraser1975, Reference Fraser1998; Storey Reference Storey1995; Gales Reference Gales2015, Reference Gales2011). The ATC in (1) can therefore be said to be not only directive, but also coercive: yet another hallmark of threatening utterances (Glukhov & Martynova Reference Glukhov and Martynova2015). The bare argument structure of (1) is also prototypical of a verbal threat: [If you (don't) X, I will Y] (Salguiero Reference Salguiero2010, Gales Reference Gales2011). Example (1) also possesses many ancillary properties of threatening utterances: (i) the intention to do harm is explicitly, directly, and unequivocally expressed; and (ii) the time, place, manner, and target of the harmful action are clearly specified (Fraser Reference Fraser1998).
By comparison, example (2) lacks many of these features. For instance, (2) does not make any overt mention of the addressor or any future harmful action he/she will undertake. Instead, it simply portends an unspecified negative event which might befall the addressee as a possible consequence of his/her own actions. If one were to take (2) on face-value alone, an equally convincing case could potentially be made for arguing that it is not a malicious threat at all but rather a neutral prediction or even a well-intended warning. Linguistic research informed by speech act theory has offered great assistance in helping to resolve such classificatory ambiguities (Shuy Reference Shuy1993, Storey Reference Storey1995, Fraser Reference Fraser1998, Walton Reference Walton2000, Salguiero Reference Salguiero2010, Gales Reference Gales2015, Berk-Seligson & Seligson Reference Berk-Seligson and Seligson2016). According to this work, the key to drawing the lines of demarcation is to examine not only the words contained in the utterance (locution), but also their collective communicative intention (illocution) and consequences (perlocution).
Using this logic, (2) may be classified as a threatening speech act, if its perlocutionary effect is intimidating to the addressee; if so, it can be reasonably deduced that the addressor's intention in making the utterance (i.e. the illocutionary point) is to harm rather than to protect (Verbrugge et al. Reference Verbrugge, Dieussaert, Schaeken and Van Belle2005, Salguiero Reference Salguiero2010). Of course, not everyone who makes a threatening utterance has the desire, capability, commitment, and/or opportunity to follow it up with an act of physical violence. This fact does not, however, nullify the existence of the previous verbal threat. Instead, the threat is simply said to be ‘infelicitous’, ‘insincere’, ‘breached’, or ‘vitiated’, but a threat nonetheless (Austin Reference Austin1955:16). Thus, as Solan & Tiersma (Reference Solan and Tiersma2005:204) remind, ‘to make a threat, the speaker does not actually have to be sincere, but need only appear sincere’ [italics in the original].
Modern-day research into impolite or conflictive speech acts reveals that speakers routinely employ linguistic strategies to amplify the illocutionary and perlocutionary force of their face-threatening utterances (Locher Reference Locher2004, Reference Locher2006; Bousfeld & Locher Reference Bousfield and Locher2008; Culpeper Reference Culpeper2009, Reference Culpeper, Capone and Mey2016; Katz Reference Katz2015; Muschalik Reference Muschalik2018). Consider the following two utterances (where (1) above is repeated as (3)):
(3) Keisha, if you move into this neighborhood, I will see to it that you wake up tomorrow to a cross-burning on your front lawn! (= (1))
(4) Hey NIGGER! If you move into this neighborhood, I will see to it that you wake up tomorrow to a cross-burning on your goddamn front lawn, you stupid fucking BLACK BITCH! Go back to AFRICA!
In example (4), the illocutionary force of the conditional threat displayed by example (3) is significantly increased – or in the words of Culpeper (Reference Culpeper2009) ‘boosted’ – through the use of profanity, blasphemy, and dysphemistic references to the target's known or presumed gender and ethnoracial identity. Further amplification of the deterrent perlocution is achieved by framing the argument structure [If you X, I will Y] with the personalized negative vocatives Hey NIGGER and the personalized negative assertion you stupid fucking BLACK BITCH followed by the mutually-reinforcing directive dismissal Go back to AFRICA!.
Of course, the mere presence of particular words or phrases cannot automatically be taken as unequivocal evidence that a particular speech act is a threat. After all, what is considered to be serious, insulting, or injurious in one speech community or communicative situation may be viewed as humorous, complimentary, or affectionate in another (Culpeper Reference Culpeper, Bousfield and Locher2008, Warner & Hirshberg Reference Warner and Hirschberg2012). The analysis of speech acts must therefore take into consideration the surrounding discursive environment. Importantly, in post-modern approaches to speech act analysis, this ‘environment’ refers not only to the larger textual narrative in which the questioned utterance appears. It also includes the historical, sociocultural, and interpersonal context in which the communication took place (Locher Reference Locher2006, Culpeper Reference Culpeper, Bousfield and Locher2008, van der Bom & Mills Reference Van der Bom and Mills2015, Berk-Seligson & Seligson Reference Berk-Seligson and Seligson2016). Going back to example (4), within a US American context, the impoliteness triggers NIGGER, BLACK BITCH and Go back to AFRICA! – particularly in combination with the proposition of a public cross-burning – carry strong, if not entirely inseparable, associations with domestic terror organizations like the Ku Klux Klan (KKK). Assuming that both the message sender and receiver were cognizant of this history, the illocutionary and perlocutionary force of example (4) would be affected. Change the context to Great Britain, Australia, or India, and the illocution and perlocution of the utterance may shift as well, although the locution remains the same. In the following section, the specific social, political, and historical context of the ATCs examined in this study is presented. In line with the abovementioned post-modern discursive investigations of impolite speech acts, this detailed information is provided to facilitate the extrapolation of ‘the emergent and situated meanings’ of the ATCs and the extraordinary conditions that precipitated them (Culpeper Reference Culpeper2011).
2. HATE-FILLED POLITICAL RHETORIC, ATCS, AND THE USA
In recent years, scholarly attention has increasingly focused upon the analysis of ATCs produced by members of extremist groups (Miller Reference Miller2008, Pennebaker Reference Pennebaker2011, Meloy Reference Meloy2014, Schuurman Reference Schuurman2015, Chiluwa Reference Chiluwa2016). Part of the reason for this focus has been the alarming incidence of deadly critical and major incidents perpetrated by offenders inspired in whole or in part by the incendiary rhetoric of charismatic leaders of underground extremist organizations (e.g. the American Nazi Party, Confederate Hammerskins, the KKK). In such cases, the offenders often see themselves as ‘foot soldiers’ in an invisible war (Cacialli Reference Cacialli2010, Meloy et al. Reference Meloy, Mohandie, Knoll and Hoffmann2015). This blind allegiance may not only be given to revered figure-heads of clandestine terrorist organizations. The political leaders of legal, well-established, governmental institutions may also serve as the object of toxic identification, especially when they resort to hate-filled, populist, rhetorical strategies common to extremist organizations. It is the recognition of this potentially lethal development that has led many to raise the warning flag in response to the increasing frequency and severity of inflammatory rhetoric used by mainstream politicians.
For many European observers, the pinnacle of incendiary political speech is the United States. Without doubt, personalized attacks against political opponents have a long, rather ignominious history (Chernow Reference Chernow2017). However, even by US American standards, the acceptable limits of combative political rhetoric were breached during the 2016 presidential election. For many, the crescendo of this political pugilism was reached in the final race between Democratic candidate Hillary Rodham Clinton and Republican Party newcomer, Donald J. Trump. In September 2016, for example, Hillary Clinton described many of Trump supporters as a ‘basket of deplorables’ made up of people with racist, sexist, homophobic, xenophobic, and Islamophobic attitudes (Reilly Reference Reilly2016: paragraph 1). For his own part, the then presidential candidate Trump also made numerous, highly controversial, deeply divisive remarks disparaging ethnoracial and religious minorities, women, immigrants, and members of the LGBT community (Cohen Reference Cohen2017, Silva Reference Silva2018). Although causality is notoriously difficult to establish, the candidates’ verbal animosities seemed to serve as powerful kindling for politically-motivated violence (Dickerson Reference Dickerson2016).
A particularly disturbing case in point occurred on June 14, 2017, when 66-year-old, dyed-in-the-wool Democrat, James Hodgkinson, opened fire during a congressional baseball game in Washington, D.C., critically injuring a police officer and several Republican lawmakers (Britt Reference Britt2017, Person Reference Persons2017, Reuters 2017). Just two months later, in Charlottesville, Virginia, James Fields, a 20-year-old, self-avowed white nationalist, plowed his car into anti-nazi demonstrators, injuring 19 and killing one: 32-year-old civil rights activist, Heather Heyer (ABC News 2017). Although on opposite sides of the political spectrum, both lone-assailants had much in common: pre-existing mental health issues, an obsessive fixation with inflammatory political rhetoric, toxic identification with a mainstream party, and a history of threatening communications (Shear, Goldman & Cochrane Reference Shear, Goldman and Cochrane2017, Sheth Reference Sheth2017).
These highly publicized acts of US domestic terrorism were viewed with considerable concern by Europeans with an eye to their own elections, their worry being that the unusually aggressive rhetorical style of the 2016 US presidential race could detrimentally affect the comportment of European politicians and their societies at-large (Aalberg et al. Reference Aalberg, Esser, Reinemann, Strömbäck and de Vreese2017). Such worries are not unfounded. Aside from the danger that overly acrimonious rhetoric by politicians may help to legitimize intolerance within mainstream society, there is also the risk that it may catalyze future acts of verbal and physical violence (European Union Agency for Fundamental Rights 2016). As Anderson-Nathe & Gharabaghi (Reference Anderson-Nathe and Gharabaghi2017:3) state:
The language and ideas presented by the newly elected or imposed leaderships in many jurisdictions around the world are those of violence. When we accept pronouncement that some amongst us are to be feared, to be rejected, to be excluded and to be watched, we are promoting not safety and well-being but violence and cultural disintegration.
Despite these dangers, psycholinguistic research into politically-motivated threatening communications has traditionally concerned itself with the potential risk private citizens pose to political leaders (e.g. Calhoun Reference Calhoun1998, Reference Calhoun2001; Borum et al. Reference Borum, Fein, Vossekuil and Berglund1999; Baumgartner et al. Reference Baumgartner, Scalora and Plank2001; Scalora et al. Reference Scalora, Baumgartner, Callaway, Zimmerman, Hatch-Maillette, Palarea, Krebs, Covell and Washington2002; Meloy, Sheridan & Hoffmann Reference Meloy, Sheridan and Hoffmann2008; Chauvin Reference Chauvin2011; Meloy Reference Meloy2014; Hoffmann, Meloy & Sheridan Reference Hoffmann, Reid Meloy and Sheridan2014). By contrast, the potential impact of high-ranking politicians’ aggressive rhetoric on the threatening communications produced by private citizens has been relatively overlooked. The purpose of this investigation is to help address this oversight.
3. RESEARCH METHODOLOGY
For the current small-scale mixed-method investigation, an original corpus of 30 English-language ATCs were compiled from an internet search of hate crimes reported in the United States during the final run-up to the 2016 US presidential election. To be included in the corpus, each anonymous exemplar had to have been received by the target(s) during November 2016, and be the subject of investigation for possible violation of a hate-crime criminal code.
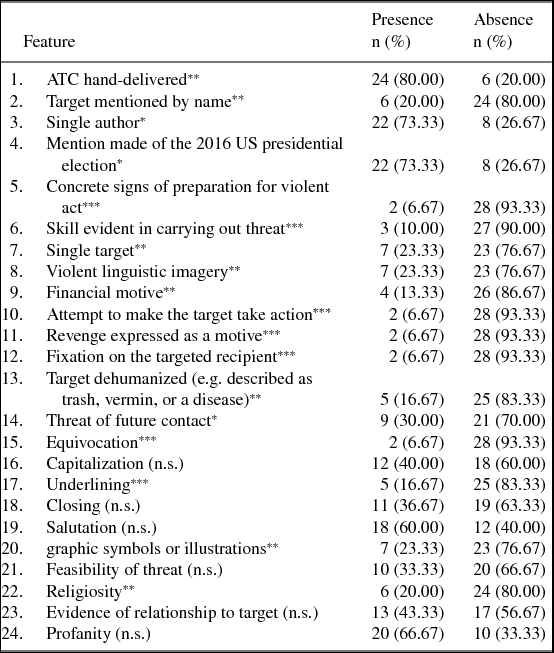
The selected letters were then manually digitalized and transcribed. Any and all errors in grammar, punctuation, and spelling identified in the original ATC texts were retained. After the transcription process, the letters were coded for statistical analyses. This analysis had three foci: (i) the format (e.g. hand-written vs. typed), formatting (e.g. typed, italics, bolding, underlining), and thematic content of the ATC; (ii) the transmission characteristics of the ATC; and (iii) the characteristics of the ATC recipient and ATC sender. Each letter was evaluated to determine the presence or absence of 24 linguistic and paralinguistic factors identified in the scientific literature and by law enforcement agencies as being potentially significant markers of ‘problematic approach behavior’ as it is formally called in threat analysis literature (Scalora et al. Reference Scalora, Baumgartner and Plank2003, Cacialli Reference Cacialli2010, Schoeneman et al. Reference Schoeneman, Scalora, Darrow, McLawsen, Chang and Zimmermann2011, Meloy Reference Meloy2014). A complete list of these variables is presented in the appendix. The results of the dichotomous coding were then used for chi-square analyses to determine which features, if any, reached the level of statistical significance. In addition to the quantitative analyses, the investigation also involved a detailed qualitative examination of threatening speech acts identified in the corpus. The varying linguistic form and function of these face-threatening performatives are illustrated with 10 sample excerpts from the corpus.
As with every investigation, this methodological design is not free of limitations. The comparatively small sample-size and scope, for example, necessarily limit the statistical power of the analyses and the generalizability of the findings. The use of a single researcher to assess the material may also have introduced unwanted subjectivity. Nevertheless, as will be demonstrated here, the combination of the quantitative approach developed by the FBI with the qualitative approach pioneered by speech acts theorists still yields many useful insights.
4. FINDINGS
The ATCs were randomly identified in and collected from 15 different states. In alphabetical order, the states represented in the corpus with the number of ATCs recovered within them is as follows: California (2), Florida (2), Georgia (2), Illinois (1), Iowa (2), Massachusetts (3), Michigan (1), Missouri (1), Nevada (1), New York (2), North Carolina (2), Texas (5), Washington (3), West Virginia (1), and Wisconsin (1). While all of the major regions of the continental US were represented, the South and the Midwest were particularly prevalent. Accounting for 16.13% of the corpus, Texas contributed the largest share of ATCs recovered for this investigation. The bulk of the communications (56.67%) were reported between the 15th and the 18th of November.
Of the ATCs in the corpus, 73.33% made explicit mention of the 2016 US presidential election and/or one of the leading candidates. The most commonly occurring proper noun in the corpus was Trump (e.g. Go TRUMP!, TRUMP COUNTRY!, Trump won!). References to the election were not always this direct, however. Sometimes, they were simple declarations that would only make sense within the post-election context (e.g. We won!).
With regard to the ATC-recipients’ identities, four different minority groups were attacked: (i) racial, ethnic, or national (13.33%); (ii) religious (20.00%); (iii) sexual orientation/gender (40.00%); and (iv) mixed (26.67%), where more than one of the aforementioned characteristics seemed to have been targeted. For example, in one instance, a family of Muslim immigrants from the Sudan was sent an ATC. In this case, it was impossible to discern whether the object of the ATC-sender's negative attention was the family's immigrant status, religion, or both. Overall, however, there seems to have been a good deal of overlap between the hatred expressed for Muslims and foreigners. A closer examination of the ATCs expressing hatred towards a racial, ethnic, or national heritage revealed that 75.00% were anti-immigrant. Moreover, in the subset of ATCs with utterances explicitly attacking a religious grouping, 66.67% were anti-Islamic and 33.33% were anti-Semitic.
It is important to note that in 33.33% of all the cases examined, the ATC targets were not identical to the ATC recipients. In one instance, for example, the same message was sent to all of the residents of a major apartment complex without regard for the individual demographic identities. An extract from this ATC is displayed below:
(5) PLEASE DO NOT SELL OR RENT YOUR HOMES TO THEM
[Muslims, Indians, Blacks, and Jews]
WE ARE EVERYWHERE AND WATCHING EVERY MOVE
In the first line of extract (5), an explicit direct request is made. According to some theorists, the realization of the request via an imperative as opposed to the more indirect communicative alternative of an interrogative (e.g. Can/Could/Would you please not sell or rent . . .) ‘already constitutes a significant breach of Anglo-American politeness norms’ (Searle Reference Searle1979, Brown & Levinson Reference Brown and Levinson1987, Leech Reference Leech1990). The use of the conventionalized politeness marker PLEASE does little to soften this effect. This initial face-threatening illocutionary act then receives immediate reinforcement in the following line. Note the aspect, tense, and mood utilized in the double declarative: the omnipresence of the message-sender is underscored by the simple present indicative which is used for expressing a constant state of being or a natural law. Along with that, the simple continuous is used for indicating that an action – in this case surveillance – is currently taking place. The cumulative perlocutionary effect is coercion and threat. The fact that the message recipients are asked for compliance does not change this effect. What is key here is that an attempt is made to secure compliance through duress (Trosborg Reference Trosborg1995).
As in the example above, in 76.67% of the cases examined, the ATCs had been hand-delivered rather than mailed via the postal service or electronic means. An examination of the locations where these ATCs had been discovered revealed that the majority (43.3%) had been delivered to the ATC recipients’ homes. Accounting for 26.67% of the sample, the second most common delivery site was the recipients’ cars. This location was followed closely by the recipients’ place of work (23.33%). Finally, 1.3% of the ATCs were left at the recipients’ place of worship. The chi-square tests revealed no significant differences in the delivery locations.
Overall, the ATCs were exceedingly short communications, with the average page length and number of words 1.10 and 61.27, respectively. The shortest communication contained only four words and the longest 1,099 words. In 66.67% of cases, the ACTs were handwritten messages scrawled on scraps of paper. A little less than one-third (30.30%) were prepared using a computer and just over one-quarter (26.67%) contained symbols, imagery, or drawings. The most common image was the swastika.
In keeping with the ‘letter-genre’, 60.00% opened with some form of salutation. However, in contrast to non-threatening written communications, these openers were more often than not pejorative (e.g. Hey Faggot, Hey Dumbass, Hey Looser, Hey). In the three instances where the standard formulaic Dear was employed, it was immediately followed by an insult (e.g. Dear Nigga (As you like to say)). Thus, from the very first line of text, the ATC recipients were confronted with verbal aggression. This combative stance was further reflected in the fact that 16.67% of the messages depicted the target as non-human (e.g. vermin, trash, a disease). However, generally speaking, the message writers preferred profanity over injurious metonymy.
In 59.90% of the ATCs, at least one instance of obscenity was utilized. The selection of vulgarities targeted four aspects of identity: sexual orientation, gender, religion, and ethnoracial identity/association (e.g. bitch, dike, faggot, hymie, nigger, nigger-lover). Aside from their surface face-threatening function, these negative vocatives were commonly used to magnify the underlying perlocutionary function of the ATCs’ primary illocutionary point (PIP). The obscenities accordingly appeared in one of three syntactic positions: (i) integrated within the PIP (25.00%); (ii) framing the PIP, immediately before and/or afterwards (43.75%); and (iii) both within and around the PIP (31.25%). Examples of each appear below:
(6) FAggoTs GeT OuT!
(7) Get out of our neighborhood NOW
FAGGOTS!!
(8) HEY FAGGOT
We won, so you better WATCH YOURE bACK. YOU'RE dAys ARE NUMbERd. YOU Will SEE you COCK SUCKER
In extract (6), the directive illocutionary act of ordering gays to leave the country is heightened by the use of the pejorative faggots at the head of the utterance. In (7), the same illocutionary act is performed; however, the perlocutionary boost appears after the directive, in the subsequent line. Extract (8) is a bit more complex. Here, a mutually-reinforcing syntactic chain of three idiomatic expressions with complementary denotative meanings is used. According to the Merriam-Webster Dictionary, the first phrase is used to tell someone to be attentive or vigilant. The second is used to say someone will ‘die, fail, or end soon’. Finally, the third is a variant of ‘just (you) wait and see’ and is used to communicate that ‘one is sure that something will happen’. Collectively, this illocutionary chain is meant to warn the target of imminent though non-descript harm. This warning does not appear to serve a benevolent purpose, though, given that it is syntactically framed by face-threatening derogatory references to the target's sexual orientation (i.e. FAGGOT and COCK SUCKER). The perlocutionary effect is therefore more likely to be intimidatory than protective.
As reported above, not all of the ATCs relied on obscenity to bolster their menacing effect. Take, for example, the following excerpt:
(9) WE ARE NAHZIIS!!! AND NOW THAT TRUMP IS PRESIDENT WE CAN KILL YOU!!!
This text utilizes the aforementioned prototypical argument structure [If you X, then I will Y] with one key difference. The condition upon which threatened negative action will take place is not predicated upon the target's future compliance with a demand made by the ATC sender. Instead, the condition has already been fulfilled by an event beyond the target's individual control (i.e. the result of the presidential election). It is upon this basis that the declaration is made: We can kill you!!! The choice in modality is critical here. Had the message utilized the future indicative (i.e. ‘We will kill you!!!’), a far higher degree of speaker intention and volition would have been communicated. By using the modal auxiliary can, ability and permissibility are emphasized instead. In other words, now that there has been a change in government and Donald Trump has been elected president, the speaker and those of his/her ilk (i.e. WE) are now free to kill the target of the message.
Note here that the explicit predicate kill is used rather than an indirect figure of speech that merely hints at a potential physical threat to life. This lexical choice lends more credence to the inference that the intended illocutionary point is to intimidate. Of course, one could argue that the purpose of the utterance was not to frighten but to forewarn. What undermines this alternative interpretation is the preceding three-word predicate nominative construction (WE ARE NAHZIIS!!!). In this concise statement, the ATC sender proclaims membership in a modern-day, violent, right-wing extremist group in the United States that takes its inspiration from the National Socialists of Europe, who, after the political ascendancy of Adolf Hitler were allowed to kill millions. By historical extension, the threatening perlocutionary effect of the utterance now . . . we can kill you!!! is effectively bolstered.
The ATC from which this text was extracted was not alone in making historical allusions to National Socialism. In the following excerpt taken from a different ATC, the same linguistic boosting strategy is used:
(10) You muslims are a vile and filthy people. Your mothers are whores and your fathers are dogs. You are evil. But, your day of reckoning has arrived. There's a new Sherriff in town - - President Donald Trump. He's going to cleanse America and make it Shine again. And, he's going to start with you muslims. He's going to do to you muslims what Hitler did to the jews. You muslims would be wise to pack your bags and get out of Dodge
After a series of personalized negative assertions about the target's family and religious heritage, the ATC goes on to ‘recite the circumstances under which the transaction is to be effected’ (Austin Reference Austin1955:7). As before, the condition for the portended negative event is described as already having been met by Donald Trump's election. The US American idiom ‘There's a new Sheriff in town’ harkens back to Hollywood Westerns in which righteous town citizens are terrorized by a gang of outlaws while corrupt officials turn a blind eye. The turning point comes when a new sheriff, typically an outsider, arrives in Dodge, the quintessential US American wild West town. The newcomer then single-handedly restores law and order. In (9), the then political outsider Donald Trump is cast in this role as savior: hence the Biblical allusion to the ‘day of reckoning’. However, in (10), the new justice forecast is not one of peace and tranquility. The protagonist is instead presented as cleansing America of Muslims who are depicted as vile and filthy. Since the introduction of the euphemism ‘ethnic cleansing’ during the Balkans Wars, this predicate is strongly associated with genocide. This connotation is immediately reinforced with the two predictions: (i) he's [Trump is] going to start with you muslims; and (ii) He's going to do to you muslims what Hitler did to the jews.
Once again, tense, aspect, and modality are key here: the use of the future indicative present progressive is commonly used in US American English to express personal purpose, aim, or intention (Alexander Reference Alexander1989), and in this case, that express intention is the repeat annihilation of a religious minority. As Austin reminds, the use of the third person singular as opposed to first person singular in the agentive role does not automatically undermine the performative nature of the utterance – threat in this case. The action of the performer must not, Austin cautions, be ‘wrongly cast into a purely grammatical mould’ (Austin Reference Austin1955:60). Following this logic, Donald Trump is a passepartout for the politically like-minded, including the ATC sender. It is against this exposition that the final act of advising the target to get out of Dodge must be analyzed. The final locution operates similarly to the familiar coercive conditional threat [You had better (not) X, or else Y]. When [Y] involves the sender taking actions that will result in the receiver's murder, the perlocutionary effect is not one of advisement but threat. Here again, much can be learned about the speech act by attending to the embedded sociocultural and historical references.
In the ATC corpus, 20.00% explicitly mentioned National Socialism. The other equally common reference was US American Slavery. An excellent example is found in (11):
(11) Now that our man TRUMP is elected and republicans own both the senate and the house – time to organize tar & feather VIGILANTE SQUADS and go arrest & torture those deviant university leaders spouting off all this Diversity Garbage.
The beginning of (11) is familiar: the condition upon which the menacing augury is predicated is said to have been fulfilled by the election results. The message then proclaims that the time has come for retribution. The agent of this action, the VIGILANTE SQUADS, is pre- and post-modified by the adjectival and verbal couplets tar & feather and arrest & torture. This syntactic mirroring helps to build a historical bridge between the past and the present calls to arms. In the US American Reconstruction Era (c. 1863–1877), for example, the KKK used tar-and-feathering in its lynching rituals to punish individuals deemed to have trespassed the lines of racial segregation (Harris Reference Harris1995). The targets of this vigilantism were carefully selected to maximize public warnings against challenging the ideology of White Supremacy (Russell-Brown Reference Russell-Brown2009). In much the same way, the grammatical and political object singled out for vigilantism in extract (11) are also community leaders: academicians. More specifically, the designated targets are those deviant university leaders who are progressively spreading or spouting off Diversity Garbage.
The ATC from which (11) was excerpted was randomly distributed across a US university campus. The meaning intended and taken no doubt shifted with the recipient. For like-minded readers on campus, the illocutionary act performed by the triple imperative to organize, arrest, and torture may have been a command to take action. The accompanying perlocutionary effect may then have been one of persuading, convincing, or inciting. For receivers who either identified as or sympathized with the projected targets, the very same locution may have a different perlocutionary effect: intimidation and threat. Thus, as stated before, the interpretation of the speech act depends upon the relationship of the message sender and recipient.
Across the entire corpus, an examination of those ATCs containing some form of linguistic threat (be it direct, veiled, specified, or unspecified) revealed that 93.33% had been articulated without linguistic equivocation or hesitation. This finding was highly significant (χ² (1) = 22.54, p ≤ .001). Nevertheless, only 10.00% contained details which would tend to indicate that the threat made was feasible or imminent. This set of findings might relate to the next. Despite the fact that 69.97% of the ATCs had been deposited on the recipients’ private property, only 43.33% of the cases showed clear evidence of a prior relationship or contact between the sender and the receiver. In one such case, the ATC sender revealed that he/she had once been an admiring high school student of the recipient and was deeply disappointed by the recipient's anti-Trump postings. This identity cue was a-typical for the corpus, however. As a general rule, prior sender–receiver contacts were indirectly (and most probably inadvertently) revealed. For example, occasionally ATCs contained private information about the recipient that could only have been known by someone in his/her immediate social circle (e.g. intimate details about the recipient's private routine or use of a private nickname). However, as a group, the ATCs contained very little detailed information about the recipients. Even basic information such as the ATC-target's personal name was statistically significant in its absence (χ² (1) = 10.8, p ≤ .05).
These results are congruent with the finding that a statistically significant minority of the ATCs made mention of an interpersonal motivation for the communication (e.g. financial recompense (13.33%), revenge (6.67%), or obvious personal fixation on the specific ATC recipient (6.67%)). Instead, the primary motivation for selecting the ATC receiver seemed to have been the ATC-senders’ desire to vent their hatred towards a particular group. Be that as it may, relatively few of the ATCs warned of a future contact (30.00%) or gave concrete evidence of preparation for a future violent act (6.67%). Both of these features were statistically significant in their absence: (χ² (1) = 22.54, p ≤ .001) and (χ² (1) = 4.8, p ≤ .05), respectively. After issuing the intended threat(s) or insult(s), most of the ATCs (63.33%) abruptly ended. An examination of those ATCs that did include closings yielded one final interesting finding: 26.67% were signed as if the ATC had been composed by a large group (e.g. America!, Trump Country, Trump Nation, and The World). This hyperbolic autonymy seems to have served the double purpose of simultaneously inflating the relational power of the ATC senders while minimizing that of their targets.
5. DISCUSSION AND CONCLUSIONS
In the past, it has proven extremely difficult to obtain large stores of authentic written material from forensic cases involving threat (e.g. extortion, blackmail, ransom, kidnapping, stalking, etc.; Nini Reference Nini2017). The compilation of large-scale forensic corpora with millions of words has been consequently thwarted. However, with the rapid proliferation of electronically transmitted messages via social media and the internet (e.g. Twitter, Facebook, and Instagram), it is now at least theoretically possible to compile large collections of ATCs. As Spitzberg & Gawron (Reference Spitzberg and Gawron2016:58) explain, ‘the larger the corpora, the more stable the results are likely to be, and the greater the opportunity to examine unique discriminating features of different types of threats’. Once important ethical and legal questions surrounding ownership, authorization, and use have been resolved, such corpora could be used for mixed-method multivariate metalinguistic analyses. Expanding on the current investigation, for example, such studies could be conceivably used for the identification, classification, and interpretation of potentially threatening linguistic utterances made by private citizens in response to politicians’ postings (e.g. Presidential Tweets). However, even in small-scale corpus-driven investigations such as the one presented here, it is possible to learn much about how language can instill feelings of anxiety and dread. As Glasgow & Schouten (Reference Glasgow and Schouten2014:44) remind, ‘the very act of sending an argumentative or hostile communication’ in and of itself ‘represents a breach of normative behavior and suggests that the sender may have difficult controlling hostile impulses and maintaining appropriate boundaries’. Aside from the risk connoted by this overarching transgression, several of the paralinguistic and linguistic features found in the ATCs could be interpreted as potentially important risk indicators for future inappropriate, potentially dangerous, behavior. For example, the fact that the majority of ATCs were left at the target's private property (e.g. home residence or car) may well indicate a disconcerting level of risk-taking behavior on the part of the ATC sender (Simon & Tunkel Reference Simons and Tunkel2014). In addition, the unequivocal use of offensive language (e.g. name-calling, insults, and threats) to belittle, intimidate, threaten, chastise, humiliate, injure, and shame the ATC recipients may indicate a troubling level of hostility. This tendency is not without importance, when one considers that verbal and physical aggression have been found to correlate (Straus Reference Straus1979, Linaker & Busche-Iversen Reference Linaker and Busche-Iversen1995, Hillbrand Reference Hillbrand2000, Scalora et al. Reference Scalora, Baumgartner and Plank2003, McNiel & Binder Reference McNiel and Binder2006, Gidycz, Warkentin & Orchowski Reference Gidycz, Warkentin and Orchowski2007). Seen together, these features could reasonably be interpreted as potential warning signals of future violence.
However, the ATC analysis also revealed several potential contra-indicators of future physical aggression (e.g. the relative absence of concrete planning, threat feasibility, and skill level) (Calhoun Reference Calhoun1998, Reference Calhoun2001, Fitzgerald Reference Fitzgerald2005). Moreover, the fact that so many of the ATCs appeared to resort to rather obvious forms of linguistic staging (e.g. suggesting that the ATC had been written by the entire US nation or even the world itself) could be interpreted as the ATC-senders’ attempt to lend strength and credibility to the communicative force behind their messages (Simons & Tunkel Reference Simons and Tunkel2014). Another finding which might be interpreted as risk mitigatory was the fact that the majority of the ATCs were conspicuously short, handwritten, notes that appeared to have been hurriedly scribbled on scraps of paper and quickly deposited in easily accessible public locations. By contrast, lengthy, carefully prepared, typewritten letters that had been placed in hard-to-access intimate spaces (e.g. the recipient's bedroom, the glove compartment of the recipient's car) were comparatively rare. This finding is important in view of the fact that detail-rich, lengthy communications with specific demands have been found to be more commonly written by people who not only threatened, but also engaged in subsequent problematic approach behaviors (e.g. Schoeneman et al. Reference Schoeneman, Scalora, Darrow, McLawsen, Chang and Zimmermann2011).
Finally, the frequent use of profane and derogatory language in the ATCs may also be a risk mitigatory sign. Contrary to popular belief, the use of abusive language has not consistently been shown to be significant predictor of future inappropriate approach behaviors (Baumgartner et al. Reference Baumgartner, Scalora and Plank2001, Scalora et al. Reference Scalora, Baumgartner and Plank2003, Schoeneman et al. Reference Schoeneman, Scalora, Darrow, McLawsen, Chang and Zimmermann2011, Gales Reference Gales2015). In fact, empirical evidence from large-scale investigations of threatening communication indicates that a polite tone is actually associated with future acts of violence (Dietz et al. Reference Dietz, Matthews, Van Duyne, Martell, Parry, Stewart, Warren and Crowder1991, Smith Reference Smith2008).
Based on this overall constellation of linguistic and situational features, the quantitative analysis of the ATCs seemed to indicate a relatively low level of risk for imminent physical violence. This does not mean to negate or in any way diminish, however, the psychological damage these verbal acts may well have done to their primary targets. Therein lies one of the major conceptual advantages of applying speech act theory to ATC analysis: it highlights the equal importance of analyzing what was said, what was meant, and what was the result (Strawson Reference Strawson1964). The context-sensitive examination of all three aspects can enrich traditional actuarial approaches to ATC analysis.
This mixed-method approach might facilitate more accurate risk estimates for future physical violence and encourage more sensitive assessments of the present-day psychosocial harm done by ATCs. This is an important point. Even if an ATC does not culminate in direct contact, the trauma of this communicative act alone can produce long-lasting and deep-seated pain, fear, suspicion, resentment, and anger in the recipient (Craig-Henderson & Sloan Reference Craig-Henderson and Sloan2003). What is more, the negative effects may extend far beyond the original target. The injury and offense may be felt by a host of secondary victims who identify as and/or with the primary target. This dynamic can help to (re)ignite inter-group tensions which can, in turn, catalyze more acts of aggression. This negative potential is, of course, not restricted to the politically embattled US.
Even within Nordic countries that have long prided themselves on their comparatively cordial tradition of political discourse, some Scandinavian observers have warned that mainstream politicians have increasingly adopted rhetorical methods once associated with extremism, be it to the left or the right (Schierup & Ålund Reference Schierup and Ålund2011, Hellström, Nilsson & Stolz Reference Hellström, Nilsson and Stoltz2012, Sakki & Pettersson Reference Sakki and Pettersson2015, Juul Christiansen Reference Juul Christiansen, Akkerman, de Lange and Rooduijn2016, Nedergaard & Wivel Reference Nedergaard and Wivel2018). As Fryklund (Reference Fryklund, Wodak, KhosravNik and Mral2013:275) observes, these changes in Nordic political rhetoric have been accompanied by a return of populism ‘both as an empirical reality and as an important research topic’. While the presidential election is over in the US, the general elections in many Nordic nations are right around the corner (Sweden: 2018, Denmark: 2019, Finland: 2019, Iceland: 2020). This timing provides an excellent opportunity for conducting analogous forensic linguistic research within Scandinavia.
ACKNOWLEDGEMENTS
The author would like to express her gratitude to Dr. T. Karoli Christensen.
APPENDIX
Table A1. Chi-square analysis of the absence and presence of (para)linguistic variables.