Crossref Citations
This article has been cited by the following publications. This list is generated based on data provided by
Crossref.
Milosevic, Tijana
Van Royen, Kathleen
and
Davis, Brian
2022.
Artificial Intelligence to Address Cyberbullying, Harassment and Abuse: New Directions in the Midst of Complexity.
International Journal of Bullying Prevention,
Vol. 4,
Issue. 1,
p.
1.
García-Fernández, Cristina María
Moreno-Moya, Miriam
Ortega-Ruiz, Rosario
and
Romera, Eva M.
2022.
Adolescent Involvement in Cybergossip: Influence on Social Adjustment, Bullying and Cyberbullying.
The Spanish Journal of Psychology,
Vol. 25,
Issue. ,
Teng, Teoh Hwai
and
Varathan, Kasturi Dewi
2023.
Cyberbullying Detection in Social Networks: A Comparison Between Machine Learning and Transfer Learning Approaches.
IEEE Access,
Vol. 11,
Issue. ,
p.
55533.
Sultan, Daniyar
Toktarova, Aigerim
Zhumadillayeva, Ainur
Aldeshov, Sapargali
Mussiraliyeva, Shynar
Beissenova, Gulbakhram
Tursynbayev, Abay
Baenova, Gulmira
and
Imanbayeva, Aigul
2023.
Cyberbullying-related Hate Speech Detection Using Shallow-to-deep Learning.
Computers, Materials & Continua,
Vol. 74,
Issue. 1,
p.
2115.
Sufi, Fahim
2023.
A New Social Media-Driven Cyber Threat Intelligence.
Electronics,
Vol. 12,
Issue. 5,
p.
1242.
Dang, Yuzhuo
Chen, Weijie
Zhang, Xin
and
Chen, Honghui
2023.
REKP: Refined External Knowledge into Prompt-Tuning for Few-Shot Text Classification.
Mathematics,
Vol. 11,
Issue. 23,
p.
4780.
Ghosh, Soumitra
Priyankar, Amit
Ekbal, Asif
and
Bhattacharyya, Pushpak
2023.
A transformer-based multi-task framework for joint detection of aggression and hate on social media data.
Natural Language Engineering,
Vol. 29,
Issue. 6,
p.
1495.
Alfurayj, Haifa Saleh
Yee, Ng Sui
and
Lutfi, Syaheerah Lebai
2023.
Bystanders Unveiled: Introducing a Comprehensive Cyberbullying Corpus with Bystander Information.
p.
1012.
Alfurayj, Haifa Saleh
and
Lutfi, Syaheerah Lebai
2023.
Exploring Bystanders' Roles in Labeled Cyberbullying Threads on Twitter: A preliminary analysis.
p.
1018.
Sufi, Fahim
2023.
Social Media Analytics on Russia–Ukraine Cyber War with Natural Language Processing: Perspectives and Challenges.
Information,
Vol. 14,
Issue. 9,
p.
485.
Kumar, Yulia
Huang, Kuan
Perez, Angelo
Yang, Guohao
Li, J. Jenny
Morreale, Patricia
Kruger, Dov
and
Jiang, Raymond
2024.
Bias and Cyberbullying Detection and Data Generation Using Transformer Artificial Intelligence Models and Top Large Language Models.
Electronics,
Vol. 13,
Issue. 17,
p.
3431.
Saleh Alfurayj, Haifa
Lebai Lutfi, Syaheerah
and
Perumal, Ramesh
2024.
A Chained Deep Learning Model for Fine-Grained Cyberbullying Detection With Bystander Dynamics.
IEEE Access,
Vol. 12,
Issue. ,
p.
105588.
Teng, Teoh Hwai
Varathan, Kasturi Dewi
and
Crestani, Fabio
2024.
A comprehensive review of cyberbullying-related content classification in online social media.
Expert Systems with Applications,
Vol. 244,
Issue. ,
p.
122644.
Hoque, Md. Nesarul
and
Seddiqui, Md. Hanif
2024.
Exploring Transformer Ensemble Approach to Classify Cyberbullying Text for the Low-resource Bengali Language.
p.
1.
Wu, Xiaodong
Wu, Hao
and
He, Pei
2024.
Leveraging Domain-Specific Word Embedding and Hate Concepts in Hate Speech Detection.
p.
1.
Singh, Divya
Gupta, Sonam
and
Gupta, Pradeep
2024.
Innovative Computing and Communications.
Vol. 1021,
Issue. ,
p.
277.
Gan, May Fen
Na Chua, Hui
Jasser, Muhammed Basheer
and
Wong, Richard T.K.
2024.
Categorization of Cyberbullying based on Intentional Dimension.
p.
285.
Wang, Runyu
Lu, Tun
Zhang, Peng
and
Gu, Ning
2025.
Role Identification Based Method for Cyberbullying Analysis in Social Edge Computing.
Tsinghua Science and Technology,
Vol. 30,
Issue. 4,
p.
1659.
Mali, Mohan K.
Pawar, Ranjeet R.
Shinde, Sandeep A.
Kale, Satish D.
Mulik, Sameer V.
Jagtap, Asmita A.
Tambewagh, Pratibha A.
and
Rajput, Punam U.
2025.
Automatic detection of cyberbullying behaviour on social media using Stacked Bi-Gru attention with BERT model.
Expert Systems with Applications,
Vol. 262,
Issue. ,
p.
125641.
Sandoval, Manuel
Abuhamad, Mohammed
Furman, Patrick
Nazari, Mujtaba
Hall, Deborah L.
and
Silva, Yasin N.
2025.
Social Networks Analysis and Mining.
Vol. 15213,
Issue. ,
p.
355.
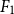 ${F_1}$-score of 55.84%, and the best one for Dutch (RobBERT) yielding an
${F_1}$-score of 55.84%, and the best one for Dutch (RobBERT) yielding an 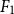 ${F_1}$-score of 56.73%. Experiment replication data and source code are available at https://osf.io/nb2r3.
${F_1}$-score of 56.73%. Experiment replication data and source code are available at https://osf.io/nb2r3.


