Published online by Cambridge University Press: 24 March 2015
The coordinate transformation offers a remarkable way to design cloaks that can steer electromagnetic fields so as to prevent waves from penetrating into the cloaked region (denoted by Ω0, where the objects inside are invisible to observers outside). The ideal circular and elliptic cylindrical cloaked regions are blown up from a point and a line segment, respectively so the transformed material parameters and the corresponding coefficients of the resulted equations are highly singular at the cloaking boundary ∂Ω0. The electric field or magnetic field is not continuous across ∂Ω0. The imposition of appropriate cloaking boundary conditions (CBCs) to achieve perfect concealment is a crucial but challenging issue.
Based upon the principle that a well-behaved electromagnetic field in the original space must be well-behaved in the transformed space as well, we obtain CBCs that intrinsically relate to the essential “pole” conditions of a singular transformation. We also find that for the elliptic cylindrical cloak, the CBCs should be imposed differently for the cosine-elliptic and sine-elliptic components of the decomposed fields. With these at our disposal, we can rigorously show that the governing equation in Ω0 can be decoupled from the exterior region 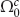 , and the total fields in the cloaked region vanish under mild conditions. We emphasize that our proposal of CBCs is different from any existing ones.
, and the total fields in the cloaked region vanish under mild conditions. We emphasize that our proposal of CBCs is different from any existing ones.
Using the exact circular (resp., elliptic) Dirichlet-to-Neumann (DtN) non-reflecting boundary conditions to reduce the unbounded domain  to a bounded domain, we introduce an accurate and efficient Fourier-Legendre spectral-element method (FLSEM) (resp., Mathieu-Legendre spectral-element method (MLSEM)) to simulate the circular cylindrical cloak (resp., elliptic cylindrical cloak). We provide ample numerical results to demonstrate that the perfect concealment of waves can be achieved for the ideal circular/elliptic cylindrical cloaks under our proposed CBCs and accurate numerical solvers.
to a bounded domain, we introduce an accurate and efficient Fourier-Legendre spectral-element method (FLSEM) (resp., Mathieu-Legendre spectral-element method (MLSEM)) to simulate the circular cylindrical cloak (resp., elliptic cylindrical cloak). We provide ample numerical results to demonstrate that the perfect concealment of waves can be achieved for the ideal circular/elliptic cylindrical cloaks under our proposed CBCs and accurate numerical solvers.