Book contents
- Frontmatter
- Contents
- Preface to the First Edition
- Preface to the Second Edition
- 1 Monoalphabetic Ciphers Using Additive Alphabets
- 2 General Monoalphabetic Substitution
- 3 Polyalphabetic Substitution
- 4 Polygraphic Systems
- 5 Transposition
- 6 RSA Encryption
- 7 Perfect Security—One-time Pads
- Appendix A Tables
- Appendix B ASCII Codes
- Appendix C Binary Numbers
- Solutions to Exercises
- Further Readings
- Index
- About the Authors
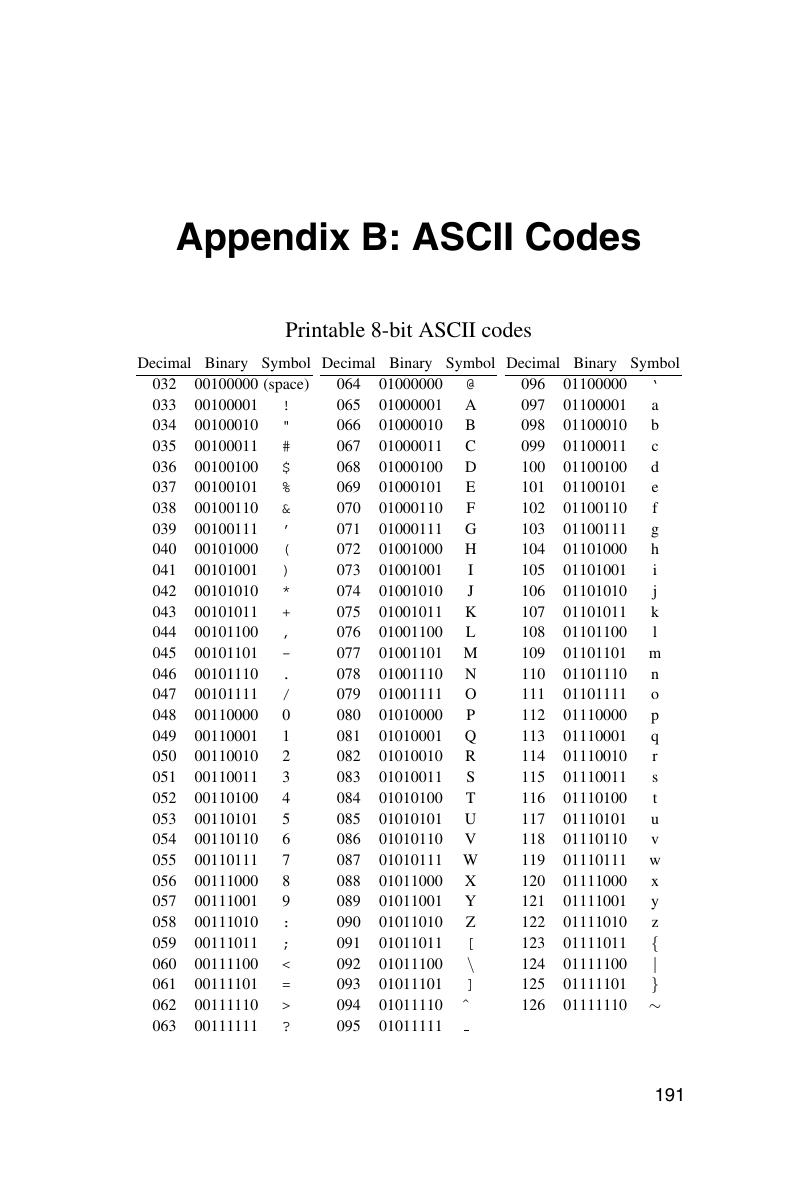
Appendix B - ASCII Codes
- Frontmatter
- Contents
- Preface to the First Edition
- Preface to the Second Edition
- 1 Monoalphabetic Ciphers Using Additive Alphabets
- 2 General Monoalphabetic Substitution
- 3 Polyalphabetic Substitution
- 4 Polygraphic Systems
- 5 Transposition
- 6 RSA Encryption
- 7 Perfect Security—One-time Pads
- Appendix A Tables
- Appendix B ASCII Codes
- Appendix C Binary Numbers
- Solutions to Exercises
- Further Readings
- Index
- About the Authors
Summary
- Type
- Chapter
- Information
- Elementary CryptanalysisA Mathematical Approach, pp. 191 - 192Publisher: Mathematical Association of AmericaPrint publication year: 2009

